Are you curious about the security of modern car technology? This article, brought to you by CAR-REMOTE-REPAIR.EDU.VN, delves into the potential vulnerabilities of keyless smart cars and explores how software-defined radio (SDR) car technology could be compromised. We’ll guide you through potential threats and effective countermeasures, offering insights into secure remote car repair and automotive cybersecurity training. Learn about RF security, wireless car entry systems, and automotive hacking prevention to enhance your skills and stay ahead in automotive technology.
Contents
- 1. Understanding Software Defined Radio (SDR) Car Technology
- 1.1 What is Software-Defined Radio (SDR)?
- 1.2 How Does SDR Car Technology Work?
- 1.3 Key Benefits of SDR in Automotive Applications
- 1.4 Common Applications of SDR in Modern Vehicles
- 2. Potential Security Risks in SDR Car Technology
- 2.1 Understanding the Attack Models
- 2.1.1 Man-in-the-Middle (MITM) Attacks
- 2.1.2 Replay Attacks
- 2.1.3 Relay Attacks
- 2.2 Identifying Threat Models
- 2.3 Key Fob Vulnerabilities
- 3. Practical Implementation of SDR Car Hacking
- 3.1 Tools Required for SDR Car Hacking
- 3.2 Step-by-Step Guide to Capturing Radio Frequencies
- 3.3 Replaying Captured Frequencies
- 4. Mitigation Models and Countermeasures
- 4.1 Rolling Codes Explained
- 4.1.1 How Rolling Codes Work
- 4.2 KeeLoq Encryption
- 4.2.1 Understanding KeeLoq Encryption
- 5. Advanced Security Measures for SDR Car Technology
- 5.1 Mutual Authentication Protocols
- 5.2 Intrusion Detection Systems (IDS)
- 5.3 Secure Over-the-Air (OTA) Updates
- 6. The Role of Automotive Cybersecurity Training
- 6.1 Essential Skills for Automotive Cybersecurity Professionals
- 6.2 Importance of Continuous Learning and Updates
- 6.3 Certifications and Training Programs
- 7. Case Studies: Real-World SDR Car Hacking Incidents
- 7.1 Analysis of the Jeep Cherokee Hack (2015)
- 7.2 Key Fob Replay Attacks: A Growing Concern
- 7.3 Impact on Vehicle Manufacturers and Consumers
- 8. The Future of SDR Car Security
- 8.1 AI-Driven Threat Detection
- 8.2 Blockchain-Based Security Solutions
- 8.3 Quantum-Resistant Encryption
- 9. Practical Tips for Securing Your Keyless Car
- 9.1 Using Signal-Blocking Pouches (Faraday Bags)
- 9.2 Disabling Keyless Entry When Not Needed
- 9.3 Keeping Vehicle Software Updated
- 10. Call to Action: Enhance Your Automotive Security Skills
- 10.1 Explore Our Training Programs
- 10.2 Contact Us for More Information
- FAQ: Software Defined Radio Car
- 1. What is software-defined radio (SDR) in the context of cars?
- 2. How can SDR technology be used to hack a car?
- 3. What are the main types of attacks that exploit SDR car technology?
- 4. What are rolling codes, and how do they protect against replay attacks?
- 5. What is KeeLoq encryption, and how does it enhance keyless entry systems?
- 6. What are some advanced security measures for SDR car technology?
- 7. What skills are essential for automotive cybersecurity professionals?
- 8. How can car owners protect their keyless vehicles from SDR-based attacks?
- 9. What is the role of AI in enhancing SDR car security?
- 10. How can blockchain technology contribute to SDR car security?
1. Understanding Software Defined Radio (SDR) Car Technology
How does software-defined radio (SDR) revolutionize car technology, and why is it crucial for modern vehicles? Software-defined radio (SDR) car technology revolutionizes car technology by replacing traditional hardware components with software-based solutions, making vehicles more adaptable, efficient, and connected. SDR technology is crucial for modern vehicles because it enables features like keyless entry, remote diagnostics, and over-the-air (OTA) updates, enhancing the driving experience and vehicle performance.
1.1 What is Software-Defined Radio (SDR)?
Software-Defined Radio (SDR) is a radio communication system where components traditionally implemented in hardware, such as modulators and detectors, are instead implemented using software on a computer or embedded system. This flexibility allows for easier updates, customization, and adaptability to different radio frequencies and protocols. SDR offers a cost-effective and versatile solution for modern communication needs.
1.2 How Does SDR Car Technology Work?
SDR car technology works by utilizing software algorithms to perform radio functions, enabling the vehicle to communicate with various devices and networks. SDR in cars manages keyless entry systems, tire pressure monitoring, and infotainment, allowing for seamless updates and customization. By using a programmable platform, SDR can adapt to new standards and security protocols, ensuring the vehicle remains up-to-date with the latest technological advancements.
1.3 Key Benefits of SDR in Automotive Applications
What are the major advantages of incorporating Software-Defined Radio (SDR) into automotive systems? SDR in automotive applications offers several key benefits including enhanced flexibility, cost efficiency, improved security, and over-the-air (OTA) update capabilities. These advantages make SDR a crucial technology for modernizing vehicle communication and control systems.
- Flexibility: SDR enables vehicles to support multiple communication standards and frequencies, allowing for seamless connectivity across different regions and networks.
- Cost Efficiency: By replacing hardware components with software, SDR reduces the need for specialized hardware, lowering manufacturing costs and streamlining vehicle design.
- Improved Security: SDR facilitates the implementation of advanced security protocols and encryption algorithms, enhancing the vehicle’s protection against cyber threats and unauthorized access.
- Over-the-Air (OTA) Updates: SDR allows for remote software updates, enabling manufacturers to improve vehicle performance, add new features, and address security vulnerabilities without requiring physical access to the vehicle.
- Enhanced Diagnostics: SDR supports advanced diagnostic capabilities, allowing for real-time monitoring of vehicle systems and remote troubleshooting, improving maintenance and reducing downtime.
- Integration with Telematics: SDR seamlessly integrates with telematics systems, enabling features such as GPS tracking, emergency assistance, and usage-based insurance, enhancing vehicle safety and convenience.
- Customization: SDR allows for personalized vehicle settings and user preferences, enabling drivers to tailor their driving experience to their individual needs and preferences.
1.4 Common Applications of SDR in Modern Vehicles
What are the typical uses of Software-Defined Radio (SDR) in today’s automobiles? Software-Defined Radio (SDR) has various uses in modern vehicles, including keyless entry systems, remote diagnostics, infotainment, and over-the-air updates. SDR enhances connectivity and adaptability, making it a vital technology for modern automobiles.
| Application | Description |
|---|---|
| Keyless Entry Systems | SDR enables secure remote locking and unlocking of vehicles, enhancing convenience and security. |
| Remote Diagnostics | SDR supports real-time monitoring of vehicle systems, enabling remote troubleshooting and predictive maintenance. |
| Infotainment | SDR provides flexible and customizable infotainment options, including streaming services, navigation, and hands-free calling. |
| Over-the-Air (OTA) Updates | SDR allows for remote software updates, enabling manufacturers to improve vehicle performance, add new features, and address security vulnerabilities without requiring physical access to the vehicle. |
| Tire Pressure Monitoring | SDR facilitates the collection and transmission of tire pressure data, improving safety and fuel efficiency. |
| Telematics | SDR integrates with telematics systems, enabling features such as GPS tracking, emergency assistance, and usage-based insurance, enhancing vehicle safety and convenience. |
| Communication Systems | SDR enables vehicles to communicate with other vehicles and infrastructure, supporting advanced driver-assistance systems (ADAS) and autonomous driving capabilities. |
| Emergency Services | SDR supports emergency communication protocols, enabling vehicles to automatically alert emergency services in the event of an accident or breakdown. |
| Vehicle Security | SDR facilitates the implementation of advanced security protocols and encryption algorithms, enhancing the vehicle’s protection against cyber threats and unauthorized access. |
| Customization | SDR allows for personalized vehicle settings and user preferences, enabling drivers to tailor their driving experience to their individual needs and preferences. |
2. Potential Security Risks in SDR Car Technology
What vulnerabilities might arise from the integration of software-defined radio (SDR) into automotive systems? SDR car technology can introduce vulnerabilities like man-in-the-middle attacks, replay attacks, and relay attacks, making vehicles susceptible to unauthorized access and control. These risks require robust security measures to protect against potential exploits.
2.1 Understanding the Attack Models
What are the common attack models that exploit vulnerabilities in keyless car systems? Common attack models that exploit vulnerabilities in keyless car systems include man-in-the-middle attacks, replay attacks, and relay attacks. These attacks can compromise vehicle security and allow unauthorized access.
2.1.1 Man-in-the-Middle (MITM) Attacks
A Man-in-the-Middle (MITM) attack is a cyberattack where the attacker intercepts and alters communication between two parties without their knowledge. In the context of SDR car technology, this involves intercepting signals between the key fob and the vehicle.
2.1.2 Replay Attacks
How do replay attacks compromise keyless entry systems in cars? Replay attacks compromise keyless entry systems by capturing and retransmitting the radio frequency signals used to lock and unlock the car, allowing unauthorized access. This type of attack exploits the vulnerability of systems that do not use rolling codes or encryption.
2.1.3 Relay Attacks
A relay attack is a type of cyberattack where an attacker intercepts and relays signals between a key fob and a vehicle to unlock or start the car without the owner’s knowledge. This attack extends the range of the key fob, allowing the attacker to operate the vehicle from a distance.
2.2 Identifying Threat Models
What are the primary threats to smart cars that utilize SDR technology? The primary threats to smart cars using SDR technology include remote vehicle takeover, unauthorized access, data theft, and disruption of safety systems. Addressing these threats requires comprehensive security measures.
- Remote Vehicle Takeover: Attackers can remotely control vehicle functions such as steering, acceleration, and braking.
- Unauthorized Access: Attackers can unlock and start the vehicle without the owner’s permission.
- Data Theft: Sensitive data such as GPS locations, communication logs, and personal information can be stolen.
- Disruption of Safety Systems: Safety-critical systems such as airbags and anti-lock brakes can be disabled or manipulated.
- Malware Installation: Malware can be installed on the vehicle’s systems, allowing for persistent access and control.
- Spying on Occupants: Attackers can monitor conversations and activities within the vehicle.
- Tracking a Vehicle: Attackers can track the vehicle’s location in real-time.
- Thwart Safety Systems: Attackers can disable or manipulate safety systems, increasing the risk of accidents.
2.3 Key Fob Vulnerabilities
What are the common vulnerabilities associated with key fobs in modern vehicles? Common vulnerabilities in key fobs include weak encryption, lack of rolling codes, and susceptibility to cloning and jamming attacks. Addressing these vulnerabilities is crucial for enhancing vehicle security.
- Lock Out a Key: Attackers can prevent a legitimate key fob from functioning.
- Brute-Force the Key Fob Algorithm: Attackers can attempt to guess the key fob’s encryption key.
- Clone the Key Fob: Attackers can create a duplicate key fob that can unlock and start the vehicle.
- Jam the Key Fob Signal: Attackers can disrupt the communication between the key fob and the vehicle.
 Car Key Fob
Car Key Fob
3. Practical Implementation of SDR Car Hacking
How can someone exploit software-defined radio (SDR) to hack into a keyless smart car? SDR car hacking can be achieved by capturing and replaying key fob radio frequencies using tools like GNURadio and HackRF, allowing unauthorized access to the vehicle. This involves analyzing and manipulating the signals transmitted between the key fob and the car.
3.1 Tools Required for SDR Car Hacking
What tools are essential for executing a successful SDR car hack? Essential tools for executing a successful SDR car hack include a software-defined radio (SDR) device such as HackRF, GNURadio software, and a computer to run the software. These tools enable the capture, analysis, and manipulation of radio frequencies.
- Software-Defined Radio (SDR) Device: A device like HackRF One is essential for capturing and transmitting radio frequencies.
- GNURadio Software: This software provides the framework for signal processing and manipulation.
- Computer: A computer is required to run the GNURadio software and control the SDR device.
- Antennas: Various antennas may be needed to optimize signal reception and transmission.
- Signal Analysis Tools: Tools like Audacity can help analyze captured audio signals.
- Programming Skills: Basic programming knowledge (e.g., Python) is helpful for customizing scripts.
3.2 Step-by-Step Guide to Capturing Radio Frequencies
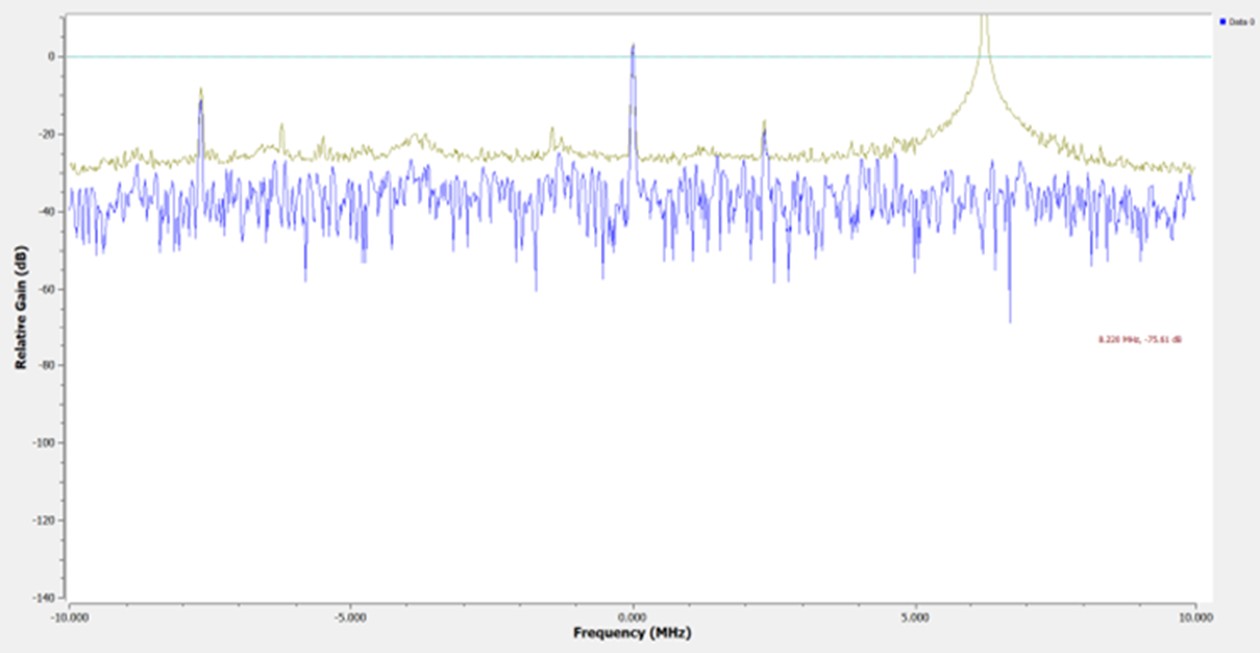
How can you effectively capture radio frequencies from a car key fob using SDR technology? To capture radio frequencies from a car key fob using SDR technology, you need to set up a flow graph in GNURadio, configure the Osmocom source to receive the key’s frequency, and use a QT GUI Waterfall Sink to visualize and record the captured signal. This process allows you to analyze and replay the key fob’s signal for unauthorized access.
- Set Up the Flow Graph: Open GNURadio Companion and create a new flow graph.
- Add Options Block: Set the ID to “top_block” and the Generate Options to “QT GUI” for a graphical interface.
- Add Osmocom Source Block:
- This block communicates with the HackRF device.
- Set the sample rate (e.g., 2M Hz).
- Specify the channel frequency of the car key (e.g., 433.9M Hz).
- Set RF Gains to 0 to avoid errors during the demo.
- Add QT GUI Waterfall Sink Block:
- This block displays the captured frequencies graphically.
- Set the Center Frequency to 0 by default.
- Set the Bandwidth to match the sample rate (e.g., 2M Hz).
- Connect the Blocks: Connect the Osmocom Source block to the QT GUI Waterfall Sink block.
- Run the Flow Graph: Execute the flow graph to start capturing frequencies.
- Capture the Key Frequency: Press the button on the car key fob to emit the frequency. Observe the peak on the QT GUI Waterfall Sink, which denotes the captured frequency.
- Store the Captured Frequencies: Use HackRF and GNURadio to store the captured frequencies in a file format on your computer for later use.
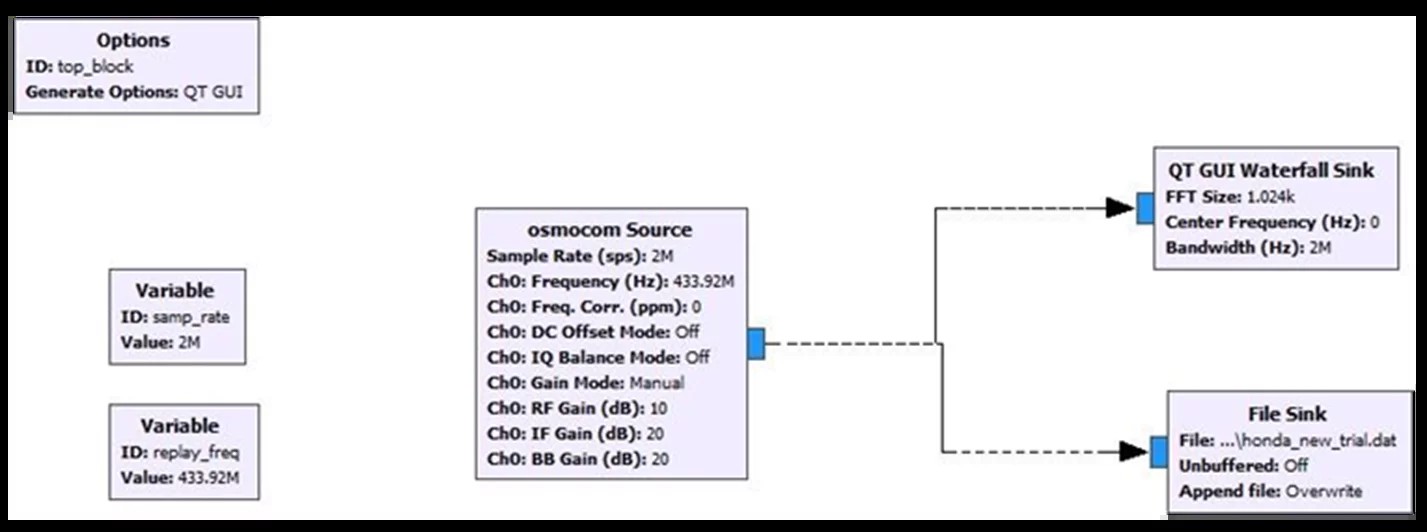 Car Hacking Flow Graph
Car Hacking Flow Graph
3.3 Replaying Captured Frequencies
What steps are involved in replaying captured frequencies to unlock a car? To replay captured frequencies and unlock a car, refine the frequencies using a throttle block, repeatedly transmit the captured signal using the HackRF, and match the required frequency to crack the lock. This process can compromise the vehicle’s security and grant unauthorized access.
- Refine Frequencies: Use a Throttle block in GNURadio to refine the captured frequencies.
- Replay Flow Graph: Create a new flow graph for replaying the captured frequencies.
- Configure Osmocom Sink: Set up an Osmocom Sink block to transmit the frequencies.
- Connect Blocks: Connect the Throttle block to the Osmocom Sink block.
- Replay Frequencies Repeatedly: Transmit the captured frequencies repeatedly using the HackRF.
- Unlock the Car: If the replayed frequency matches the car’s required frequency, the car will unlock.
4. Mitigation Models and Countermeasures
What security measures can be implemented to mitigate risks associated with SDR car hacking? Mitigation models and countermeasures include rolling codes, KeeLoq encryption, and advanced authentication protocols to protect against replay, relay, and man-in-the-middle attacks. These measures enhance the security of keyless entry systems and prevent unauthorized access.
4.1 Rolling Codes Explained
How do rolling codes enhance the security of keyless entry systems? Rolling codes enhance the security of keyless entry systems by generating a new, unpredictable code for each use, preventing attackers from replaying captured signals to gain unauthorized access. This method ensures that each transmission is unique and valid only once.
4.1.1 How Rolling Codes Work
Rolling codes, also known as hopping codes, are a mechanism used in keyless smart cars to prevent replay and relay attacks. The system works by generating a new, unpredictable code for each use.
- Pseudo-Random Number Generation: A crypto-graphically secure pseudo-random number is generated at both the transmitter (key fob) and receiver (car) ends.
- Sequential Code Transmission: The transmitter sends the next number code in sequence.
- Code Comparison: The receiver compares the received code to its calculated next number code.
- Tolerance for Missed Codes: A typical implementation compares within the next 256 codes in case the receiver missed some transmitted keys.
4.2 KeeLoq Encryption
What role does KeeLoq encryption play in securing keyless entry systems? KeeLoq encryption secures keyless entry systems by encrypting the data transmitted between the key fob and the vehicle, making it difficult for attackers to intercept and replicate the signal. This encryption method adds a layer of security against replay and relay attacks.
4.2.1 Understanding KeeLoq Encryption
KeeLoq is a proprietary block cipher used in keyless entry systems to encrypt the communication between the key fob and the vehicle.
- Encryption Process: KeeLoq encoders encrypt a 0-filled 32-bit block with the KeeLoq cipher to produce a 32-bit “hopping code.”
- Initialization Vector: A 32-bit initialization vector is linearly added (XORed) to the 32 least significant bits of the key prior to encryption and after decryption.
- Counter Mechanism: The Counter shields the frequency numeric code from being captured. When the encoder detects the press of a button, it reads the input and increments the Sync Counter value.
- Random Code Generation: The counter and keys are input to the encryption algorithm, and the output is a 32-bit data that changes with every press of the button, making the code randomly hopping and generated.
- Data Combination: This 32-bit code is combined with a fixed 34-bit portion containing information about the serial number from which the code is transmitted to the receiver.
5. Advanced Security Measures for SDR Car Technology
What advanced security measures can be employed to fortify SDR car technology against sophisticated cyber threats? Advanced security measures include implementing mutual authentication, intrusion detection systems, and secure over-the-air (OTA) update mechanisms. These strategies enhance the resilience of SDR car technology against potential exploits.
5.1 Mutual Authentication Protocols
How do mutual authentication protocols enhance the security of SDR car systems? Mutual authentication protocols enhance the security of SDR car systems by requiring both the key fob and the vehicle to verify each other’s identities before establishing a communication link, preventing unauthorized access. This ensures that only legitimate devices can interact with the vehicle’s systems.
5.2 Intrusion Detection Systems (IDS)
How do Intrusion Detection Systems (IDS) protect SDR car systems from cyber threats? Intrusion Detection Systems (IDS) protect SDR car systems by monitoring network traffic and system behavior for malicious activities, alerting security personnel to potential cyber threats. This enables timely responses and prevents unauthorized access.
5.3 Secure Over-the-Air (OTA) Updates
What measures ensure the security of Over-the-Air (OTA) updates in SDR car technology? Secure Over-the-Air (OTA) updates in SDR car technology ensure updates are authenticated and encrypted, preventing malicious software from being installed. This safeguards vehicle systems from vulnerabilities and potential cyberattacks.
6. The Role of Automotive Cybersecurity Training
How does specialized automotive cybersecurity training contribute to safeguarding modern vehicles? Automotive cybersecurity training equips professionals with the knowledge and skills to identify vulnerabilities, implement security measures, and respond to cyber threats, ensuring the protection of modern vehicles. This training is essential for addressing the evolving landscape of automotive cybersecurity.
6.1 Essential Skills for Automotive Cybersecurity Professionals
What key skills are crucial for professionals in the automotive cybersecurity field? Key skills for automotive cybersecurity professionals include threat modeling, penetration testing, secure coding, and knowledge of automotive network protocols. These skills enable them to effectively protect vehicles from cyber threats.
6.2 Importance of Continuous Learning and Updates
Why is continuous learning crucial in the field of automotive cybersecurity? Continuous learning is crucial in automotive cybersecurity because the threat landscape is constantly evolving, requiring professionals to stay updated on the latest vulnerabilities, attack techniques, and security measures. This ensures that they can effectively protect vehicles from emerging cyber threats.
6.3 Certifications and Training Programs
What certifications and training programs are available for aspiring automotive cybersecurity experts? Certifications and training programs for automotive cybersecurity experts include Certified Ethical Hacker (CEH), CompTIA Security+, and specialized courses focusing on automotive security standards and protocols. These programs provide the necessary skills and knowledge for professionals in this field.
7. Case Studies: Real-World SDR Car Hacking Incidents
What real-world incidents highlight the potential risks of SDR car hacking? Real-world incidents, such as the Jeep Cherokee hack in 2015 and various key fob replay attacks, highlight the potential risks of SDR car hacking. These cases demonstrate the importance of robust security measures in modern vehicles.
7.1 Analysis of the Jeep Cherokee Hack (2015)
What key lessons were learned from the 2015 Jeep Cherokee hack? The 2015 Jeep Cherokee hack taught the industry critical lessons about the importance of network segmentation, secure remote access, and proactive vulnerability management in automotive systems. This incident emphasized the need for robust security measures to protect modern vehicles from cyber threats.
7.2 Key Fob Replay Attacks: A Growing Concern
How prevalent are key fob replay attacks, and what makes them a growing concern in automotive security? Key fob replay attacks are increasingly prevalent due to their simplicity and effectiveness, making them a growing concern in automotive security. These attacks exploit vulnerabilities in keyless entry systems, allowing unauthorized access to vehicles.
7.3 Impact on Vehicle Manufacturers and Consumers
How do car hacking incidents affect vehicle manufacturers and consumers alike? Car hacking incidents can severely affect vehicle manufacturers by damaging their reputation and increasing costs for recalls and security upgrades, while consumers face risks of theft, privacy breaches, and compromised safety. Addressing these issues requires robust cybersecurity measures.
8. The Future of SDR Car Security
How is the future of SDR car security evolving to address emerging cyber threats? The future of SDR car security involves advancements in AI-driven threat detection, blockchain-based security, and quantum-resistant encryption to address emerging cyber threats. These innovations aim to create more resilient and secure automotive systems.
8.1 AI-Driven Threat Detection
How does AI-driven threat detection improve the security of SDR car systems? AI-driven threat detection improves the security of SDR car systems by analyzing patterns and anomalies in real-time to identify and respond to potential cyber threats, providing a proactive defense against evolving attacks. This advanced approach enhances the overall security posture of modern vehicles.
8.2 Blockchain-Based Security Solutions
What role can blockchain technology play in enhancing SDR car security? Blockchain technology can enhance SDR car security by providing a decentralized, tamper-proof ledger for managing vehicle data and verifying software updates, ensuring the integrity and security of automotive systems. This innovative approach adds a layer of trust and transparency to vehicle cybersecurity.
8.3 Quantum-Resistant Encryption
How will quantum-resistant encryption protect SDR car systems from future cyber threats? Quantum-resistant encryption will protect SDR car systems from future cyber threats by using cryptographic algorithms that are resistant to attacks from quantum computers, ensuring the long-term security of vehicle communication and data. This forward-thinking approach is essential for maintaining robust cybersecurity in the face of technological advancements.
9. Practical Tips for Securing Your Keyless Car
What practical steps can car owners take to enhance the security of their keyless vehicles? Car owners can enhance the security of their keyless vehicles by using signal-blocking pouches for key fobs, disabling keyless entry when not needed, and regularly updating vehicle software. These simple measures can significantly reduce the risk of cyberattacks.
9.1 Using Signal-Blocking Pouches (Faraday Bags)
How effective are signal-blocking pouches in preventing key fob relay attacks? Signal-blocking pouches, also known as Faraday bags, effectively prevent key fob relay attacks by blocking the radio signals emitted by the key fob, making it impossible for attackers to intercept and amplify the signal. This provides a simple yet effective layer of security for keyless entry systems.
9.2 Disabling Keyless Entry When Not Needed
Why is it advisable to disable keyless entry when the feature is not required? Disabling keyless entry when not needed reduces the risk of relay attacks by preventing the constant transmission of radio signals, making it more difficult for attackers to intercept and exploit the signal. This simple measure enhances the overall security of the vehicle.
9.3 Keeping Vehicle Software Updated
Why is it important to regularly update vehicle software? Regularly updating vehicle software is crucial because updates often include security patches that address known vulnerabilities, protecting the vehicle from potential cyberattacks and ensuring optimal performance. This proactive approach helps maintain the security and reliability of modern vehicles.
10. Call to Action: Enhance Your Automotive Security Skills
Ready to take your automotive security skills to the next level? CAR-REMOTE-REPAIR.EDU.VN offers comprehensive training programs designed to equip you with the knowledge and expertise to protect modern vehicles from cyber threats. Don’t wait, enhance your remote auto repair abilities and stay ahead in this rapidly evolving field.
10.1 Explore Our Training Programs
What training programs does CAR-REMOTE-REPAIR.EDU.VN offer to enhance automotive security skills? CAR-REMOTE-REPAIR.EDU.VN offers a range of training programs designed to enhance automotive security skills, covering topics such as threat modeling, penetration testing, and secure coding practices. These programs provide hands-on experience and expert instruction to prepare you for the challenges of automotive cybersecurity.
10.2 Contact Us for More Information
Want to learn more about our training programs and services? Contact us today at CAR-REMOTE-REPAIR.EDU.VN or visit our location at 1700 W Irving Park Rd, Chicago, IL 60613, United States. You can also reach us via WhatsApp at +1 (641) 206-8880. Let us help you enhance your automotive security skills and protect modern vehicles from cyber threats.
FAQ: Software Defined Radio Car
1. What is software-defined radio (SDR) in the context of cars?
Software-defined radio (SDR) in cars is a technology that uses software to perform radio communication functions, enabling features like keyless entry, remote diagnostics, and over-the-air updates.
2. How can SDR technology be used to hack a car?
SDR technology can be used to hack a car by capturing and replaying radio frequencies from the key fob, allowing unauthorized access to the vehicle.
3. What are the main types of attacks that exploit SDR car technology?
The main types of attacks that exploit SDR car technology include man-in-the-middle attacks, replay attacks, and relay attacks.
4. What are rolling codes, and how do they protect against replay attacks?
Rolling codes are a security mechanism that generates a new, unpredictable code for each use, preventing attackers from replaying captured signals to gain unauthorized access.
5. What is KeeLoq encryption, and how does it enhance keyless entry systems?
KeeLoq encryption is a proprietary block cipher used in keyless entry systems to encrypt the communication between the key fob and the vehicle, making it difficult for attackers to intercept and replicate the signal.
6. What are some advanced security measures for SDR car technology?
Advanced security measures include implementing mutual authentication, intrusion detection systems, and secure over-the-air (OTA) update mechanisms.
7. What skills are essential for automotive cybersecurity professionals?
Essential skills include threat modeling, penetration testing, secure coding, and knowledge of automotive network protocols.
8. How can car owners protect their keyless vehicles from SDR-based attacks?
Car owners can use signal-blocking pouches for key fobs, disable keyless entry when not needed, and regularly update vehicle software.
9. What is the role of AI in enhancing SDR car security?
AI-driven threat detection improves the security of SDR car systems by analyzing patterns and anomalies in real-time to identify and respond to potential cyber threats.
10. How can blockchain technology contribute to SDR car security?
Blockchain technology can enhance SDR car security by providing a decentralized, tamper-proof ledger for managing vehicle data and verifying software updates, ensuring the integrity and security of automotive systems.