Blocking software using Windows Firewall on Windows 7 is achievable, and CAR-REMOTE-REPAIR.EDU.VN can guide you through the process. This article will explore how to use Windows Firewall to control which applications can access the internet, enhancing your system’s security and preventing unauthorized software from communicating online. Learn how to manage network permissions, bolster internet security, and ensure secure application management.
Contents
- 1. Understanding Windows Firewall
- What Exactly is Windows Firewall?
- Why Should You Use Windows Firewall?
- How Does Windows Firewall Work?
- 2. Essential Steps Before Blocking Software
- Making Sure Windows Firewall is Enabled
- Understanding Inbound and Outbound Rules
- Creating a System Restore Point
- 3. Step-by-Step Guide to Blocking Software
- Accessing Windows Firewall Settings
- Creating a New Inbound Rule
- Specifying the Program Path
- Blocking the Connection
- Applying the Rule to Profiles
- Naming and Describing the Rule
- Creating a New Outbound Rule
- Specifying the Program Path for Outbound Rule
- Blocking the Connection for Outbound Rule
- Applying the Outbound Rule to Profiles
- Naming and Describing the Outbound Rule
- 4. Testing the New Firewall Rules
- Verifying the Blocked Connection
- Using Ping and Traceroute
- Checking Application Behavior
- 5. Managing and Modifying Firewall Rules
- Finding Existing Rules
- Disabling or Deleting Rules
- Modifying Rule Properties
- 6. Advanced Firewall Configuration
- Configuring Logging
- Using Connection Security Rules
- Working with Multiple Profiles
- 7. Troubleshooting Common Issues
- Software Not Working After Blocking
- Firewall Blocking Essential Services
- Conflicting Firewall Rules
- 8. Advanced Tips and Tricks
- Using the Command Line (Netsh)
- Creating Batch Scripts for Firewall Management
- Monitoring Firewall Activity in Real-Time
- 9. Why Choose CAR-REMOTE-REPAIR.EDU.VN for Automotive Repair Expertise
- Comprehensive Training Programs
- Expert Instructors
- State-of-the-Art Facilities
- Remote Diagnostic and Repair Training
- Continuing Education and Support
- 10. Frequently Asked Questions (FAQs)
- Can I block all internet access for a program?
- What happens when I block a program with the firewall?
- How do I unblock a program in Windows Firewall?
- Will blocking a program affect other programs on my computer?
- Is it safe to disable Windows Firewall?
- How do I know if a program is trying to access the internet?
- What are the best practices for managing Windows Firewall rules?
- Can I use Windows Firewall to block access to specific websites?
- Does Windows Firewall protect against all types of security threats?
- How do I restore Windows Firewall to its default settings?
1. Understanding Windows Firewall
What Exactly is Windows Firewall?
Windows Firewall is a built-in security system designed to monitor and control network traffic, preventing unauthorized access to your computer or network. According to Microsoft’s official documentation, the Windows Firewall helps protect your computer by blocking unauthorized programs from accessing the network. It acts as a barrier between your computer and the outside world, examining incoming and outgoing network traffic and blocking anything that doesn’t meet its pre-defined security rules.
Why Should You Use Windows Firewall?
Utilizing Windows Firewall offers several key advantages. Firstly, it provides a fundamental layer of defense against external threats, ensuring only authorized applications can communicate over the network. Secondly, it is a cost-effective solution since it is included with the Windows operating system, removing the need for additional security software. Finally, it enhances overall system stability by preventing malicious or poorly coded applications from compromising your network connection. A study by the SANS Institute found that properly configured firewalls can significantly reduce the risk of network intrusions.
How Does Windows Firewall Work?
Windows Firewall operates by inspecting network packets and comparing them against a set of rules. These rules dictate which types of traffic are allowed or blocked based on factors such as the source and destination IP addresses, ports, and protocols. According to Cisco’s security guidelines, a firewall acts as a gatekeeper, controlling access to your network by enforcing these rules. By default, Windows Firewall blocks unsolicited incoming connections, but you can configure it to block outgoing connections as well, providing a more comprehensive security posture.
 Windows Firewall settings
Windows Firewall settings
2. Essential Steps Before Blocking Software
Making Sure Windows Firewall is Enabled
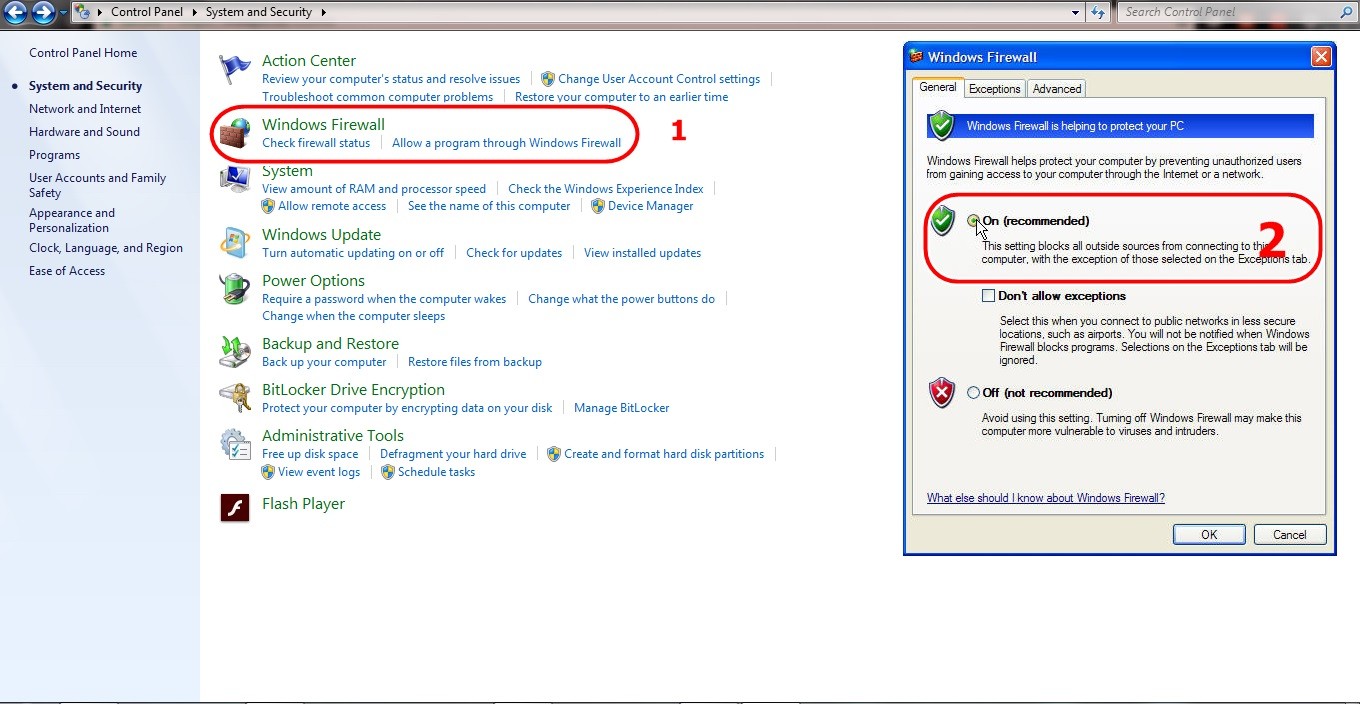
First, verify that Windows Firewall is active to ensure your system is protected.
- Go to Control Panel and click on System and Security.
- Select Windows Firewall.
- Ensure that the firewall status is set to On (recommended). If it is off, click on Turn Windows Firewall on or off in the left pane and select the Turn on Windows Firewall option for both private and public networks.
Understanding Inbound and Outbound Rules
Understanding the difference between inbound and outbound rules is crucial for effectively managing your firewall. Inbound rules control incoming connections to your computer, while outbound rules govern outgoing connections. According to the National Institute of Standards and Technology (NIST), properly configuring both inbound and outbound rules is essential for a robust security posture. By default, Windows Firewall blocks unsolicited inbound connections, but you may need to create specific outbound rules to prevent certain applications from sending data over the network.
Creating a System Restore Point
Before making any significant changes to your system settings, creating a system restore point is wise. This allows you to revert to a previous state if something goes wrong.
- Type “Create a restore point” in the Windows search bar and open the System Properties window.
- Click on the System Protection tab.
- If protection is turned off for your system drive, select it and click Configure, then choose Turn on system protection.
- Click Create, enter a name for the restore point, and click Create again.
This safety net ensures you can undo any unintended consequences from modifying firewall settings.
3. Step-by-Step Guide to Blocking Software
Accessing Windows Firewall Settings
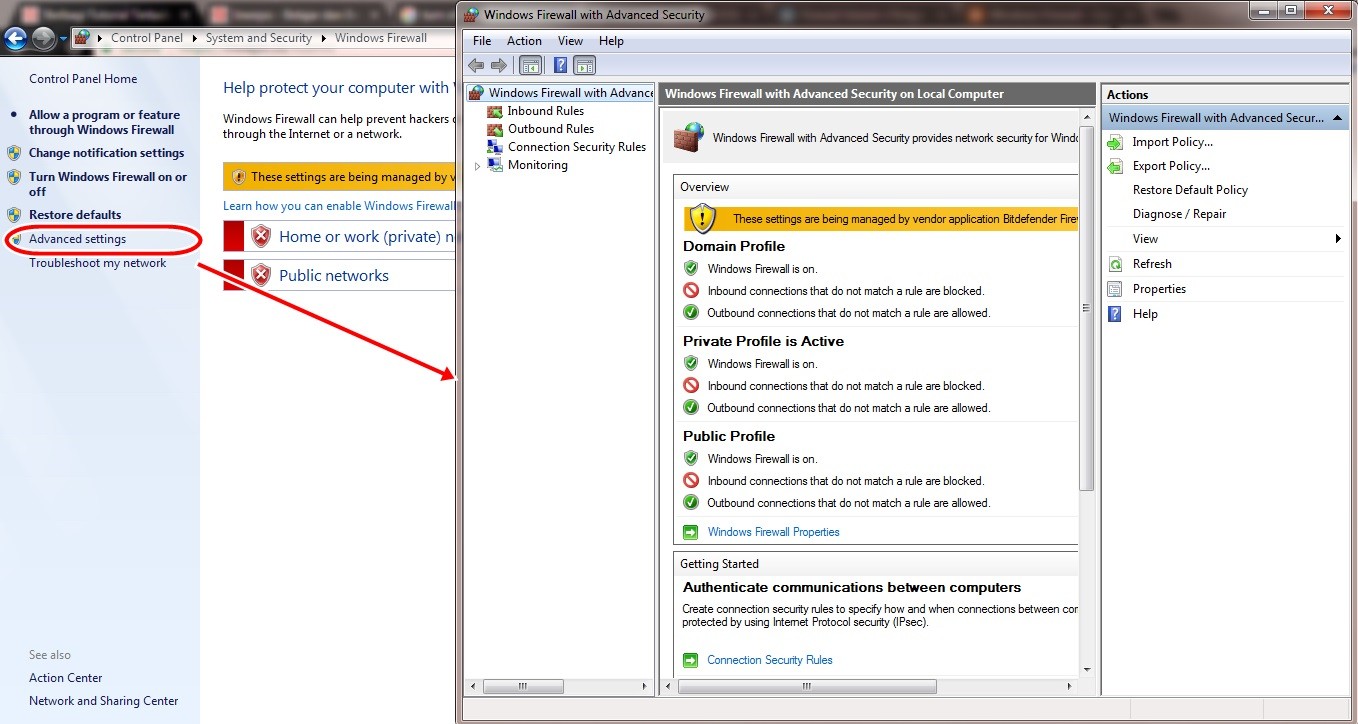
To start blocking software, you need to access the advanced settings of Windows Firewall.
- Open Control Panel.
- Click on System and Security.
- Select Windows Firewall.
- In the left pane, click on Advanced settings. This will open the “Windows Firewall with Advanced Security” window.
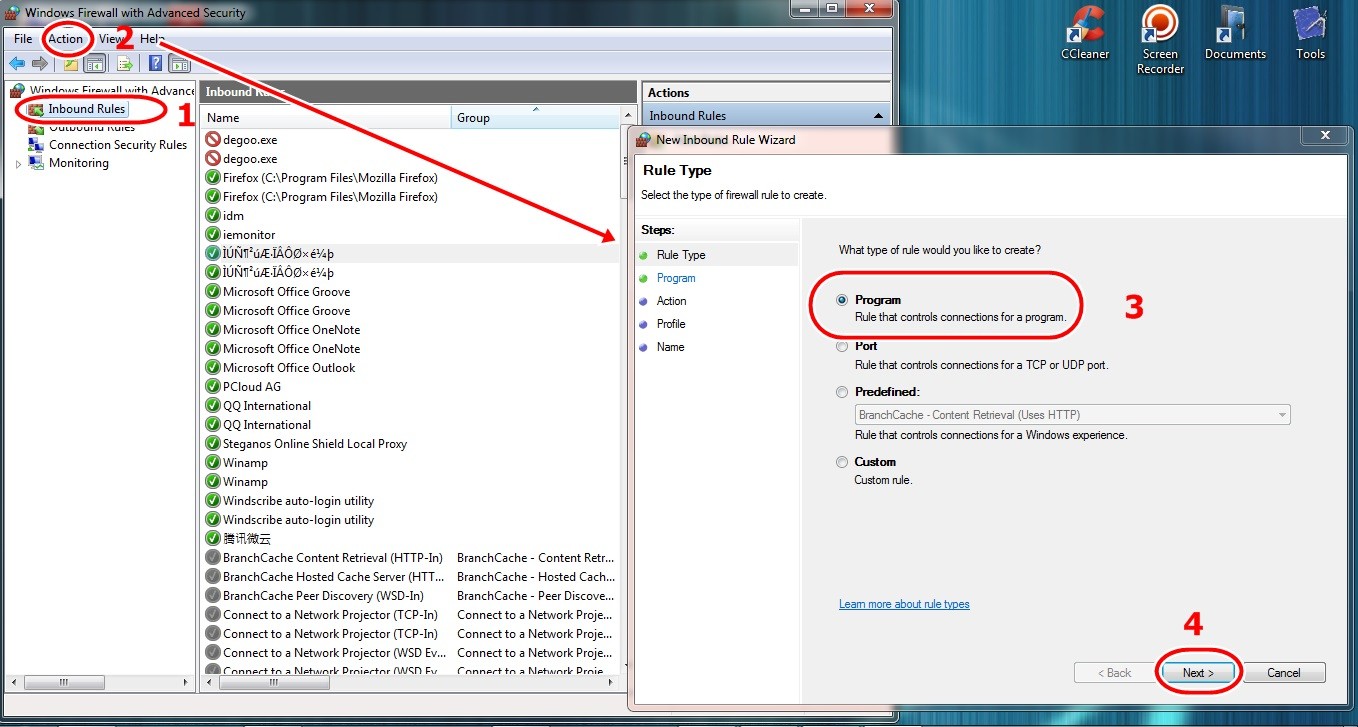
Creating a New Inbound Rule
Inbound rules control the connections that are allowed to come into your computer. Blocking inbound connections can prevent unauthorized access to specific software.
- In the “Windows Firewall with Advanced Security” window, select Inbound Rules in the left pane.
- In the right pane, click on New Rule….
- The “New Inbound Rule Wizard” will open. Select Program and click Next.
 New Inbound Rule Wizard
New Inbound Rule Wizard
Specifying the Program Path
Next, you need to specify the exact path of the program you want to block.
- In the “Program” step, select This program path:.
- Click Browse… and navigate to the location of the program’s executable file (usually in the C:Program Files or C:Program Files (x86) directory).
- Select the program and click Open, then click Next.
Blocking the Connection
Now, you can choose to block the connection.
- In the “Action” step, select Block the connection and click Next. This prevents the program from receiving any inbound connections.
Applying the Rule to Profiles
Choose when the rule should be applied.
- In the “Profile” step, ensure all options (Domain, Private, and Public) are checked. This ensures the rule applies to all network types. Click Next.
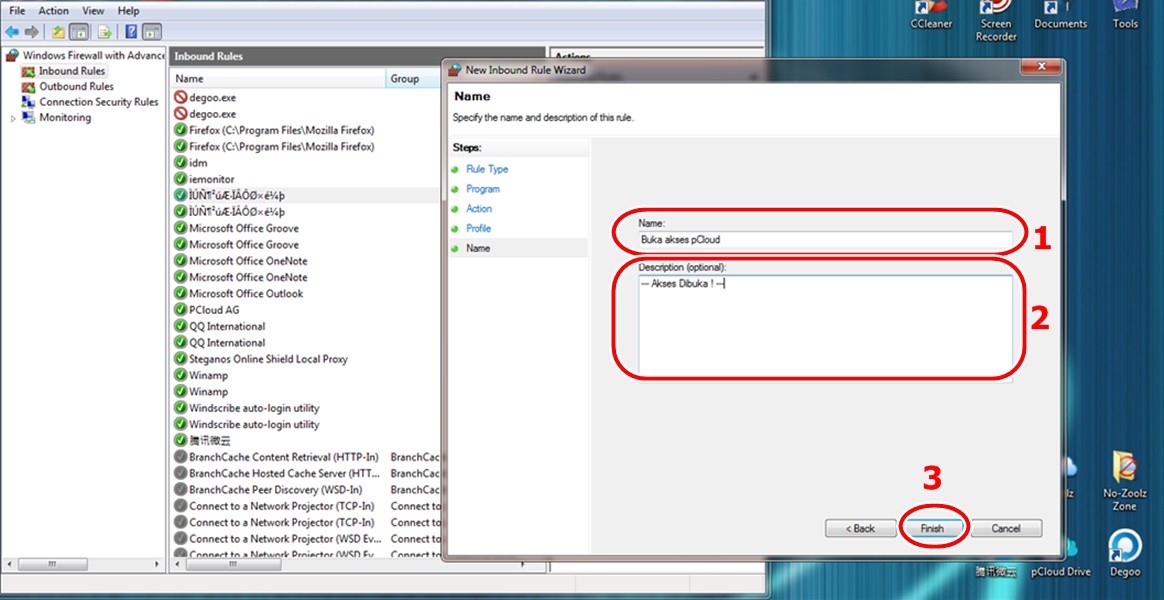
Naming and Describing the Rule
Finally, give your rule a descriptive name and, optionally, a description.
- In the “Name” step, enter a name for the rule (e.g., “Block [Program Name] Inbound”).
- Add a description if you like, then click Finish.
 Naming the rule
Naming the rule
Creating a New Outbound Rule
Outbound rules control the connections that are allowed to leave your computer. Blocking outbound connections can prevent specific software from sending data over the internet.
- In the “Windows Firewall with Advanced Security” window, select Outbound Rules in the left pane.
- In the right pane, click on New Rule….
- The “New Outbound Rule Wizard” will open. Select Program and click Next.
Specifying the Program Path for Outbound Rule
As with the inbound rule, specify the program’s path.
- In the “Program” step, select This program path:.
- Click Browse… and navigate to the location of the program’s executable file.
- Select the program and click Open, then click Next.
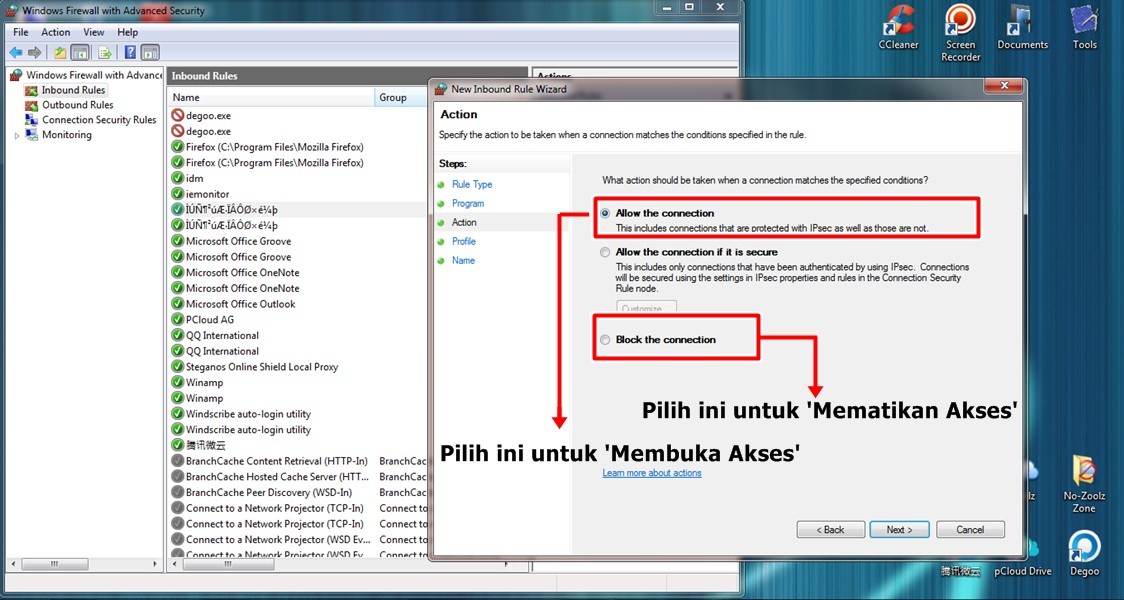
Blocking the Connection for Outbound Rule
Choose to block the outbound connection.
- In the “Action” step, select Block the connection and click Next. This prevents the program from initiating any outbound connections.
 Blocking connections
Blocking connections
Applying the Outbound Rule to Profiles
Apply the rule to all network types.
- In the “Profile” step, ensure all options (Domain, Private, and Public) are checked. Click Next.
Naming and Describing the Outbound Rule
Give your outbound rule a descriptive name.
- In the “Name” step, enter a name for the rule (e.g., “Block [Program Name] Outbound”).
- Add a description if you like, then click Finish.
4. Testing the New Firewall Rules
Verifying the Blocked Connection
After creating the inbound and outbound rules, it’s crucial to test whether the software is indeed blocked. Try to run the application and observe its behavior. If the rules are correctly configured, the application should be unable to access the internet or network resources.
Using Ping and Traceroute
To further verify the blocked connection, you can use command-line tools like ping and traceroute. Open Command Prompt and try to ping a known internet address (e.g., ping google.com). If the application is successfully blocked, the ping request should time out. Similarly, you can use traceroute to trace the route of network packets. If the application is blocked, the trace will fail to reach its destination. These tests confirm the effectiveness of your firewall rules.
Checking Application Behavior
Observe the behavior of the blocked application. Does it display an error message indicating a network connection failure? Does it crash or freeze when attempting to access the internet? These signs indicate that the firewall rules are working as expected. Additionally, check the Windows Firewall logs to see if the blocked application is attempting to make connections. This provides further evidence that the rules are being enforced.
5. Managing and Modifying Firewall Rules
Finding Existing Rules
To manage or modify existing firewall rules, return to the “Windows Firewall with Advanced Security” window.
- Select either Inbound Rules or Outbound Rules in the left pane, depending on which type of rule you want to manage.
- The right pane will display a list of all existing rules, including their names, status (enabled or disabled), and the profiles they apply to.
Disabling or Deleting Rules
If you want to temporarily disable a rule, right-click on it and select Disable Rule. To permanently delete a rule, right-click on it and select Delete. Be careful when deleting rules, as this can affect the network access of other applications.
Modifying Rule Properties
To modify the properties of a rule, such as the program path or the action (allow or block), double-click on the rule or right-click and select Properties. This will open a window where you can change various settings, including:
- General: Enable or disable the rule.
- Programs and Services: Change the program path or specify a service to which the rule applies.
- Action: Change the action to allow or block the connection.
- Profiles: Change the profiles to which the rule applies (Domain, Private, Public).
- Scope: Specify the IP addresses or ports to which the rule applies.
- Advanced: Configure advanced settings such as edge traversal and logging.
6. Advanced Firewall Configuration
Configuring Logging
Enabling logging allows you to track which connections are being blocked or allowed by the firewall. This can be useful for troubleshooting network issues or identifying potential security threats.
- In the “Windows Firewall with Advanced Security” window, right-click on Windows Firewall with Advanced Security in the left pane and select Properties.
- In the “Windows Firewall Properties” window, go to the General tab.
- Click Customize… next to “Logging”.
- Specify the location of the log file, the maximum file size, and whether to log dropped packets, successful connections, or both. Click OK to save the changes.
Using Connection Security Rules
Connection security rules allow you to configure more advanced security policies, such as requiring authentication or encryption for certain types of network traffic. This can be useful for protecting sensitive data or ensuring that only authorized users can access specific network resources.
Working with Multiple Profiles
Windows Firewall supports multiple profiles, each with its own set of rules. The active profile depends on the type of network to which your computer is connected (Domain, Private, or Public). You can configure different rules for each profile to provide different levels of security depending on the network environment. For example, you might want to allow more connections on your home network (Private profile) than on a public Wi-Fi network (Public profile).
7. Troubleshooting Common Issues
Software Not Working After Blocking
If you block a program and it stops working as expected, it may be because the firewall is blocking essential network connections. To resolve this issue, you can either disable the rule or modify it to allow specific types of traffic.
- Open the “Windows Firewall with Advanced Security” window and locate the rule you created for the program.
- Double-click on the rule to open its properties.
- Go to the Scope tab and check if the IP addresses or ports are too restrictive. You may need to allow connections from specific IP addresses or ports that the program uses.
- If you’re unsure which connections to allow, you can temporarily disable the rule and see if the program starts working. If it does, you can then re-enable the rule and gradually add exceptions until the program works correctly.
Firewall Blocking Essential Services
Sometimes, the firewall may block essential services, such as Windows Update or antivirus software. To resolve this issue, you may need to create specific rules to allow these services to communicate over the network. Consult the documentation for the specific service to determine which ports and protocols it requires.
Conflicting Firewall Rules
Conflicting firewall rules can cause unexpected behavior, such as blocking connections that should be allowed or allowing connections that should be blocked. To resolve this issue, you can review your firewall rules and look for any rules that may be conflicting with each other. Pay attention to the order of the rules, as the firewall processes rules in the order they are listed.
8. Advanced Tips and Tricks
Using the Command Line (Netsh)
For advanced users, the command line tool netsh provides a powerful way to manage Windows Firewall. You can use netsh to create, modify, and delete firewall rules, as well as configure other firewall settings.
- Open Command Prompt as an administrator.
- Type
netsh advfirewall firewallto enter the firewall context. - Use commands like
add rule,delete rule, andshow ruleto manage firewall rules. For example, to add a rule to block a program, you can use the following command:
netsh advfirewall firewall add rule name="Block Program" dir=out program="C:Program FilesProgramNameprogram.exe" action=blockCreating Batch Scripts for Firewall Management
You can create batch scripts to automate common firewall tasks, such as creating or deleting multiple rules at once. This can save time and effort, especially if you need to configure the firewall on multiple computers.
Monitoring Firewall Activity in Real-Time
Several third-party tools allow you to monitor firewall activity in real-time. These tools can provide valuable insights into the types of traffic that are being blocked or allowed by the firewall, as well as any potential security threats.
9. Why Choose CAR-REMOTE-REPAIR.EDU.VN for Automotive Repair Expertise
Comprehensive Training Programs
CAR-REMOTE-REPAIR.EDU.VN offers extensive training programs designed to elevate your automotive repair skills. Whether you’re a novice or an experienced technician, our courses cover a wide array of topics, including advanced diagnostics, remote repair techniques, and the latest automotive technologies.
Expert Instructors
Our instructors are seasoned professionals with years of experience in the automotive industry. They bring real-world knowledge and practical insights to the classroom, ensuring you receive top-notch training that prepares you for the challenges of modern automotive repair.
State-of-the-Art Facilities
We provide state-of-the-art facilities equipped with the latest diagnostic tools and equipment. This hands-on experience ensures you’re proficient in using the tools and technologies necessary to excel in remote automotive repair.
Remote Diagnostic and Repair Training
Our specialized remote diagnostic and repair training programs teach you how to diagnose and repair vehicles from a remote location. This innovative approach allows you to expand your service offerings and cater to a wider customer base.
Continuing Education and Support
We offer continuing education opportunities to keep you updated with the latest industry trends and technologies. Additionally, our support team is always available to assist you with any technical issues or questions you may have.
 Firewall advanced security
Firewall advanced security
10. Frequently Asked Questions (FAQs)
Can I block all internet access for a program?
Yes, by creating both inbound and outbound rules in Windows Firewall to block the specific program.
What happens when I block a program with the firewall?
The program will be unable to send or receive data over the network, which may affect its functionality.
How do I unblock a program in Windows Firewall?
Find the rule you created for the program in the “Windows Firewall with Advanced Security” window, right-click on it, and select “Disable Rule” or “Delete”.
Will blocking a program affect other programs on my computer?
No, blocking a program will only affect that specific program’s ability to access the network.
Is it safe to disable Windows Firewall?
Disabling Windows Firewall is not recommended, as it can leave your computer vulnerable to security threats.
How do I know if a program is trying to access the internet?
You can use a network monitoring tool or check the Windows Firewall logs to see which programs are attempting to make connections.
What are the best practices for managing Windows Firewall rules?
Use descriptive names for your rules, keep your rules organized, and regularly review your rules to ensure they are still needed.
Can I use Windows Firewall to block access to specific websites?
While Windows Firewall is primarily designed to block programs, you can use it in conjunction with other tools or techniques to block access to specific websites.
Does Windows Firewall protect against all types of security threats?
Windows Firewall provides a basic level of protection against network-based threats, but it is not a substitute for comprehensive security software, such as antivirus and anti-malware programs.
How do I restore Windows Firewall to its default settings?
In the “Windows Firewall with Advanced Security” window, right-click on “Windows Firewall with Advanced Security” in the left pane and select “Restore Default Policy”.
Securing your Windows 7 system by blocking specific software with Windows Firewall is a practical step toward enhancing your digital safety. By following the detailed steps outlined in this guide, you can effectively manage which applications access the internet, mitigating potential risks and maintaining control over your network. Remember, for comprehensive automotive repair expertise and training, visit CAR-REMOTE-REPAIR.EDU.VN.
Ready to take your automotive repair skills to the next level? Contact CAR-REMOTE-REPAIR.EDU.VN today to explore our training programs and remote support services. Our expert instructors and state-of-the-art facilities will equip you with the knowledge and skills you need to excel in the modern automotive industry.
Address: 1700 W Irving Park Rd, Chicago, IL 60613, United States. Whatsapp: +1 (641) 206-8880. Website: CAR-REMOTE-REPAIR.EDU.VN. Boost your expertise in automotive diagnostics, network security, and remote assistance with us.