Are you wondering how to make trial software a full version? It involves understanding software licensing, exploring ethical methods, and potentially seeking educational resources like those offered at CAR-REMOTE-REPAIR.EDU.VN for advanced skills. By understanding the types of software and the vendor’s intent, you can assess if you can extend the usage or upgrade the software. This also increases your chances of learning remote auto repair and diagnostic skills, software manipulation, and ethical considerations.
Contents
- 1. What Does It Mean to Convert Trial Software to Full Version?
- Understanding Trial Software Limitations
- The Importance of Ethical Considerations
- 2. What Are the Legal and Ethical Methods to Convert Trial Software?
- Purchasing a License
- Educational Programs and Discounts
- Special Promotions and Bundles
- Staying Compliant and Avoiding Risks
- 3. What Are Some Software Licensing Models?
- Perpetual Licenses
- Subscription Licenses
- Open-Source Licenses
- Understanding License Terms
- Choosing the Right Licensing Model
- 4. Are There Tools That Can Help Manage Software Licenses?
- Key Features of License Management Tools
- Popular License Management Tools
- Benefits of Using License Management Tools
- Selecting the Right Tool
- 5. What Is Software Cracking and Why Is It Illegal?
- The Process of Software Cracking
- Why Software Cracking Is Illegal
- The Risks of Using Cracked Software
- Ethical Considerations
- 6. How Do Software Vendors Protect Their Products?
- Licensing and Activation
- Copy Protection Techniques
- Anti-Tamper Technologies
- Legal Measures
- Staying Ahead of Crackers
- 7. Can Modifying Software Files Lead to Security Vulnerabilities?
- Introduction of Bugs
- Bypassing Security Measures
- Compatibility Issues
- Malware Injection
- Legal and Ethical Implications
- Best Practices
- 8. What Is Reverse Engineering and Why Is It Risky?
- The Process of Reverse Engineering
- Legitimate Uses of Reverse Engineering
- Risks of Reverse Engineering
- Legal Considerations
- Ethical Considerations
- Mitigation Measures
- 9. How Can I Protect My Own Software from Being Cracked?
- Strong Encryption
- Code Obfuscation
- Anti-Debugging Techniques
- Licensing and Activation
- Watermarking
- Legal Measures
- Regular Updates
- Monitoring and Vigilance
- 10. Where Can I Learn Advanced Software Repair and Diagnostic Skills?
- Specialized Training Programs
- Vocational Schools and Technical Colleges
- Online Courses and Tutorials
- Industry Certifications
- Hands-On Experience
- FAQ: Converting Trial Software to Full Version
1. What Does It Mean to Convert Trial Software to Full Version?
Converting trial software to a full version means unlocking all the features and removing limitations imposed by the trial period or functionality restrictions. Generally, it involves purchasing a license or obtaining a valid product key to activate the software fully.
Understanding Trial Software Limitations
Trial software typically comes with specific limitations designed to encourage users to purchase the full version. These limitations can include:
- Time Restrictions: The software is fully functional for a limited period (e.g., 30 days).
- Feature Restrictions: Certain features are disabled or limited in functionality.
- Usage Restrictions: Restrictions on the number of times the software can be used or the amount of data that can be processed.
- Nag Screens: Frequent pop-up messages reminding the user to purchase the full version.
According to a study by the Software & Information Industry Association (SIIA), these limitations are strategically implemented to provide a balance between offering a valuable trial experience and motivating users to convert to the paid version. The goal is to give potential customers a taste of the software’s capabilities while ensuring they see the value in upgrading.
The Importance of Ethical Considerations
It’s crucial to emphasize that bypassing these limitations through unauthorized methods is illegal and unethical. Software developers invest significant time and resources in creating software, and using it without proper licensing undermines their efforts.
Ethical considerations include:
- Respecting Intellectual Property: Recognizing that software is a product of intellectual effort and is protected by copyright laws.
- Supporting Developers: Paying for software ensures developers can continue to improve and update their products.
- Avoiding Legal Risks: Using unauthorized methods to bypass trial limitations can lead to legal consequences, including fines and lawsuits.
2. What Are the Legal and Ethical Methods to Convert Trial Software?
The legal and ethical methods to convert trial software to a full version involve obtaining a valid license through purchase, educational programs, or special promotions offered by the software vendor. This ensures compliance with copyright laws and supports the software developers’ efforts.
Purchasing a License
The most straightforward and ethical way to convert trial software is by purchasing a license from the software vendor. This typically involves:
- Visiting the Vendor’s Website: Navigate to the official website of the software developer.
- Selecting a License: Choose the appropriate license type based on your needs (e.g., individual, business, educational).
- Completing the Purchase: Follow the online instructions to complete the purchase, providing payment information as required.
- Receiving a Product Key: Upon successful payment, you will receive a product key or activation code.
- Activating the Software: Enter the product key into the trial software to unlock the full version.
Many vendors offer different licensing options to cater to various user needs. For example, Adobe offers subscription-based licenses through its Creative Cloud, while Microsoft provides both subscription and perpetual licenses for its Office suite.
Educational Programs and Discounts
Some software vendors offer educational programs and discounts to students, educators, and educational institutions. These programs often provide access to full versions of software at reduced prices or even for free.
Examples of educational programs include:
- Autodesk Education: Provides free access to Autodesk software for students and educators.
- Microsoft Imagine Academy: Offers training and certification programs in Microsoft technologies for educational institutions.
- Adobe Education: Provides discounts and resources for students and educators using Adobe Creative Cloud.
To take advantage of these programs, you typically need to verify your educational status through a student ID, enrollment verification, or other documentation.
Special Promotions and Bundles
Software vendors frequently offer special promotions and bundles to attract new customers or reward existing ones. These promotions can include discounts on full versions of software, bundled packages with additional software or services, or limited-time offers.
Ways to find special promotions and bundles include:
- Checking the Vendor’s Website: Regularly visit the software vendor’s website for announcements of promotions and deals.
- Subscribing to Newsletters: Sign up for the vendor’s email newsletter to receive updates on promotions and special offers.
- Following Social Media: Follow the vendor’s social media accounts (e.g., Facebook, Twitter) for announcements of promotions and deals.
- Visiting Online Marketplaces: Check online marketplaces like Amazon, Best Buy, and Newegg for discounted software and bundled packages.
Staying Compliant and Avoiding Risks
Adhering to legal and ethical methods ensures that you are using software in compliance with copyright laws and licensing agreements. This helps you avoid legal risks, such as fines, lawsuits, and reputational damage.
Furthermore, using licensed software provides access to:
- Software Updates: Regular updates that fix bugs, improve performance, and add new features.
- Technical Support: Access to customer support resources for assistance with technical issues.
- Security Patches: Security updates that protect against viruses, malware, and other security threats.
By choosing to obtain software licenses through legitimate means, you contribute to the sustainability of the software industry and ensure that you have access to the best possible software experience.
3. What Are Some Software Licensing Models?
Software licensing models determine how users are permitted to use software. Common models include perpetual licenses, subscription licenses, and open-source licenses, each with its own terms and conditions.
Perpetual Licenses
A perpetual license allows the user to use a specific version of the software indefinitely after paying a one-time fee. While the user owns the license to use the software, they do not own the software itself. Key characteristics include:
- One-Time Payment: Users pay a single fee for the license.
- Indefinite Use: The license is valid for the lifetime of the software version.
- No Automatic Updates: Users may need to pay an additional fee for upgrades to newer versions.
Perpetual licenses are common for software like Microsoft Office (though Microsoft increasingly promotes subscription-based models) and older versions of Adobe Creative Suite.
Subscription Licenses
A subscription license grants the user the right to use the software for a specific period (e.g., monthly, annually) in exchange for recurring payments. Key characteristics include:
- Recurring Payments: Users pay a fee regularly (e.g., monthly or annually).
- Access to Updates: Subscribers typically receive access to the latest software updates and new features.
- License Termination: The license expires if payments are not maintained.
Subscription licenses are increasingly popular, especially for cloud-based software like Adobe Creative Cloud, Microsoft 365, and many SaaS (Software as a Service) applications.
Open-Source Licenses
Open-source licenses grant users the rights to use, modify, and distribute the software freely. These licenses promote collaboration and innovation. Key characteristics include:
- Free Usage: The software is available for free.
- Modification Rights: Users can modify the source code to suit their needs.
- Distribution Rights: Users can distribute the software, often with certain conditions.
Examples of open-source licenses include the GNU General Public License (GPL), the MIT License, and the Apache License. Open-source software is widely used in operating systems (e.g., Linux), web servers (e.g., Apache), and programming languages (e.g., Python).
Understanding License Terms
Each software license comes with specific terms and conditions that govern how the software can be used. It’s crucial to read and understand these terms to ensure compliance and avoid legal issues. Key aspects of license terms include:
- Number of Users: Specifies the number of users who can use the software under the license.
- Geographic Restrictions: May limit the use of the software to specific geographic regions.
- Commercial Use: Defines whether the software can be used for commercial purposes.
- Redistribution Rights: Specifies whether the software can be redistributed to others.
According to the BSA (The Software Alliance), a global organization dedicated to promoting software compliance, understanding license terms is essential for both individual users and organizations to avoid copyright infringement and ensure responsible software use.
Choosing the Right Licensing Model
Selecting the right licensing model depends on your specific needs and budget. Consider the following factors:
- Budget: Perpetual licenses require a larger upfront investment, while subscription licenses offer a lower initial cost but ongoing expenses.
- Update Requirements: Subscription licenses provide access to the latest updates, while perpetual licenses may require additional upgrade fees.
- Flexibility: Subscription licenses offer more flexibility, allowing you to scale your software usage up or down as needed.
- Long-Term Use: If you plan to use the software for an extended period, a perpetual license may be more cost-effective.
By carefully evaluating these factors, you can choose the licensing model that best fits your requirements and ensures you are using software in a compliant and cost-effective manner.
4. Are There Tools That Can Help Manage Software Licenses?
Yes, software license management tools are designed to help organizations track, manage, and optimize their software licenses, ensuring compliance and cost-effectiveness.
Key Features of License Management Tools
Software license management tools offer a range of features to help organizations manage their software licenses effectively. These features include:
- License Tracking: Automatically discovers and tracks all software licenses within the organization.
- Compliance Monitoring: Ensures compliance with software licensing agreements and identifies potential violations.
- Usage Monitoring: Monitors software usage to identify underutilized licenses that can be reallocated or retired.
- Reporting: Generates reports on license usage, compliance status, and cost savings opportunities.
- Alerting: Provides alerts when licenses are nearing expiration or when usage exceeds the terms of the license agreement.
According to a report by Gartner, organizations that implement software license management tools can reduce their software costs by as much as 30% through better license utilization and compliance management.
Popular License Management Tools
Several software license management tools are available in the market, each with its own strengths and capabilities. Some of the most popular tools include:
- FlexNet Manager: A comprehensive license management solution that supports a wide range of software vendors and licensing models.
- Snow License Manager: Provides detailed insights into software usage and helps organizations optimize their license investments.
- ManageEngine License Manager: Offers automated license tracking and compliance monitoring at an affordable price.
- Aspera License Management: Focuses on optimizing software spending and reducing the risk of non-compliance.
Benefits of Using License Management Tools
Implementing software license management tools offers several benefits for organizations, including:
- Cost Savings: Optimizing license utilization and avoiding overspending on software licenses.
- Compliance Assurance: Ensuring compliance with software licensing agreements and avoiding legal penalties.
- Improved Visibility: Gaining better visibility into software assets and usage patterns.
- Reduced Risk: Minimizing the risk of security vulnerabilities and data breaches associated with unauthorized software.
- Streamlined Management: Automating license management tasks and freeing up IT resources for other priorities.
Selecting the Right Tool
Choosing the right software license management tool depends on the specific needs and requirements of your organization. Consider the following factors when evaluating different tools:
- Software Coverage: Ensure the tool supports the software vendors and licensing models used in your organization.
- Scalability: Choose a tool that can scale to meet the needs of your organization as it grows.
- Integration: Select a tool that integrates with your existing IT infrastructure and management systems.
- Ease of Use: Opt for a tool that is easy to use and requires minimal training.
- Cost: Compare the pricing models of different tools and choose one that fits your budget.
By carefully evaluating these factors and selecting the right software license management tool, organizations can improve their software asset management practices, reduce costs, and ensure compliance with software licensing agreements.
5. What Is Software Cracking and Why Is It Illegal?
Software cracking is the process of modifying software to remove or bypass its copy protection mechanisms, such as license checks, serial number validation, or trial period limitations. This is illegal because it violates copyright laws and software licensing agreements.
The Process of Software Cracking
Software cracking typically involves reverse engineering the software to understand its copy protection mechanisms and then modifying the code to disable or bypass them. Crackers often distribute these modified versions of the software online, allowing others to use the software without paying for a license.
Techniques used in software cracking include:
- Reverse Engineering: Analyzing the software’s code to understand how it works and identify vulnerabilities.
- Patching: Modifying the software’s code to disable or bypass copy protection mechanisms.
- Keygen Generation: Creating programs that generate valid serial numbers or activation codes for the software.
- Loader Modification: Altering the software’s loader to bypass license checks or trial period limitations.
Why Software Cracking Is Illegal
Software cracking is illegal for several reasons:
- Copyright Infringement: Software is protected by copyright laws, which grant the copyright holder exclusive rights to reproduce, distribute, and modify the software. Cracking software violates these rights.
- Violation of Licensing Agreements: Software is typically licensed to users under specific terms and conditions, which prohibit unauthorized modification or distribution. Cracking software violates these licensing agreements.
- Loss of Revenue for Developers: When software is cracked, developers lose revenue from legitimate sales, which can hinder their ability to invest in future development and innovation.
- Security Risks: Cracked software often contains malware or other malicious code that can compromise the security of the user’s system.
According to the Copyright Act, copyright infringement can result in civil penalties, including monetary damages, and criminal penalties, including fines and imprisonment.
The Risks of Using Cracked Software
Using cracked software carries several risks:
- Security Risks: Cracked software may contain viruses, Trojans, spyware, or other malicious code that can harm your system and compromise your data.
- Lack of Updates: Cracked software typically does not receive updates or security patches, making it vulnerable to newly discovered security threats.
- Instability: Cracked software may be unstable and prone to crashes or errors, leading to data loss and reduced productivity.
- Legal Consequences: Using cracked software can result in legal penalties, including fines and lawsuits.
- Lack of Support: Users of cracked software do not have access to technical support or customer service.
Ethical Considerations
Beyond the legal risks, using cracked software is also unethical. Software developers invest significant time and resources in creating software, and using it without paying undermines their efforts. Supporting developers through legitimate purchases helps ensure they can continue to improve and update their products.
Furthermore, using cracked software can contribute to a culture of piracy and disrespect for intellectual property rights, which can harm the software industry and stifle innovation.
6. How Do Software Vendors Protect Their Products?
Software vendors employ various methods to protect their products from unauthorized use and piracy, including licensing, activation, and copy protection techniques.
Licensing and Activation
Licensing and activation are fundamental methods used to control access to software and ensure that only authorized users can use it.
- Product Keys: Software vendors issue unique product keys or serial numbers that users must enter during installation or activation. These keys are used to verify the legitimacy of the software license.
- Online Activation: Many software products require online activation, where the software connects to the vendor’s servers to verify the license and activate the software. This process helps prevent the use of counterfeit or pirated software.
- License Managers: Some software vendors use license managers to control the distribution and usage of their software. License managers can track the number of licenses in use, enforce license terms, and prevent unauthorized access.
Copy Protection Techniques
Software vendors use various copy protection techniques to prevent unauthorized duplication and distribution of their software. These techniques include:
- Encryption: Encrypting the software code to make it difficult for crackers to reverse engineer and modify it.
- Code Obfuscation: Obfuscating the software code to make it harder to understand and analyze.
- Hardware Locking: Tying the software license to specific hardware components, such as the CPU or hard drive.
- Digital Watermarking: Embedding hidden watermarks in the software code to identify unauthorized copies.
Anti-Tamper Technologies
Anti-tamper technologies are designed to detect and prevent unauthorized modifications to the software code. These technologies include:
- Checksum Verification: Calculating checksums of the software code and verifying them at runtime to detect any unauthorized changes.
- Code Integrity Checks: Performing regular checks of the software code to ensure that it has not been tampered with.
- Runtime Protection: Protecting the software code at runtime to prevent debugging, reverse engineering, and other forms of tampering.
According to a study by Irdeto, a company specializing in digital platform security, anti-tamper technologies can significantly increase the cost and complexity of cracking software, making it less attractive to pirates.
Legal Measures
In addition to technical measures, software vendors also use legal measures to protect their products from piracy. These measures include:
- Copyright Enforcement: Pursuing legal action against individuals and organizations that engage in software piracy.
- Digital Millennium Copyright Act (DMCA): Using the DMCA to take down websites and online services that distribute or promote cracked software.
- End User License Agreements (EULAs): Enforcing the terms of EULAs, which prohibit unauthorized modification, distribution, or use of the software.
Staying Ahead of Crackers
Software vendors must continuously update their protection measures to stay ahead of crackers who are constantly developing new techniques to bypass them. This requires ongoing investment in research and development and a proactive approach to security.
According to a report by the Business Software Alliance (BSA), software piracy costs the global economy billions of dollars each year. By implementing effective protection measures, software vendors can reduce piracy rates and protect their revenue streams.
7. Can Modifying Software Files Lead to Security Vulnerabilities?
Yes, modifying software files can lead to security vulnerabilities because it can introduce unintended bugs, bypass security measures, and create compatibility issues.
Introduction of Bugs
Modifying software files, especially without a thorough understanding of the code, can introduce unintended bugs that can cause the software to malfunction or crash. These bugs can create unexpected behavior and potentially expose the system to security vulnerabilities.
For example, a simple typo in the modified code can lead to a buffer overflow, which can allow an attacker to execute arbitrary code on the system.
Bypassing Security Measures
Modifying software files can bypass security measures that are designed to protect the software and the system it runs on. By disabling or removing these security measures, the software becomes more vulnerable to attacks.
For example, modifying a software file to bypass a license check can also disable other security features, such as code integrity checks, making it easier for attackers to inject malicious code.
Compatibility Issues
Modifying software files can create compatibility issues with other software or hardware components. This can lead to instability and reduced performance, as well as security vulnerabilities.
For example, modifying a system file to change its behavior can cause conflicts with other system components, leading to crashes or unexpected behavior.
Malware Injection
Modified software files can be used to inject malware into the system. Attackers can modify the software to include malicious code that can steal data, install backdoors, or perform other malicious activities.
For example, an attacker can modify a popular software application to include a Trojan horse that installs a backdoor on the system, allowing the attacker to gain remote access.
Legal and Ethical Implications
Modifying software files without authorization can also have legal and ethical implications. It can violate copyright laws and licensing agreements and can expose the user to legal penalties.
Furthermore, modifying software files without authorization can be considered unethical, as it undermines the efforts of the software developers and can harm the software industry.
Best Practices
To avoid security vulnerabilities when modifying software files, it is important to follow best practices:
- Obtain Authorization: Obtain authorization from the software vendor before modifying any software files.
- Understand the Code: Thoroughly understand the code before making any modifications.
- Test Thoroughly: Test the modified software thoroughly to ensure that it is stable and does not introduce any new vulnerabilities.
- Use Secure Coding Practices: Use secure coding practices to minimize the risk of introducing bugs or vulnerabilities.
- Keep Software Updated: Keep software updated with the latest security patches to protect against known vulnerabilities.
According to the SANS Institute, a leading provider of information security training and certification, following these best practices can significantly reduce the risk of security vulnerabilities when modifying software files.
8. What Is Reverse Engineering and Why Is It Risky?
Reverse engineering is the process of analyzing software or hardware to understand its design, function, and operation. While it can be used for legitimate purposes, it is also risky because it can violate copyright laws, expose security vulnerabilities, and lead to the creation of malicious software.
The Process of Reverse Engineering
Reverse engineering typically involves disassembling or decompiling the software to view its source code or machine code. This allows the engineer to understand how the software works and identify its key components.
Techniques used in reverse engineering include:
- Disassembly: Converting machine code into assembly language to make it more readable.
- Decompilation: Converting machine code into a higher-level programming language, such as C or Java.
- Debugging: Using debugging tools to step through the code and observe its behavior.
- Static Analysis: Analyzing the code without executing it to identify potential vulnerabilities or design flaws.
- Dynamic Analysis: Analyzing the code while it is running to observe its behavior and identify runtime errors.
Legitimate Uses of Reverse Engineering
Reverse engineering can be used for legitimate purposes, such as:
- Software Interoperability: Understanding how different software systems work to enable them to interoperate.
- Security Auditing: Identifying security vulnerabilities in software to improve its security.
- Bug Fixing: Understanding the cause of software bugs to fix them.
- Educational Purposes: Learning how software works by analyzing its code.
- Patent Analysis: Determining whether a software product infringes on existing patents.
Risks of Reverse Engineering
Reverse engineering can also be risky for several reasons:
- Copyright Infringement: Reverse engineering software without authorization can violate copyright laws, which grant the copyright holder exclusive rights to reproduce, distribute, and modify the software.
- Exposure of Security Vulnerabilities: Reverse engineering can expose security vulnerabilities in software, which can be exploited by attackers to compromise the system.
- Creation of Malicious Software: Reverse engineering can be used to create malicious software, such as viruses, Trojans, and spyware.
- Violation of Licensing Agreements: Reverse engineering software can violate the terms of licensing agreements, which prohibit unauthorized modification or distribution of the software.
- Legal Penalties: Engaging in unauthorized reverse engineering can result in legal penalties, including fines and imprisonment.
Legal Considerations
The legality of reverse engineering depends on the specific circumstances and the laws of the jurisdiction. In general, reverse engineering is permitted for interoperability purposes, but it is prohibited for purposes that violate copyright laws or licensing agreements.
The Digital Millennium Copyright Act (DMCA) in the United States prohibits the circumvention of technological measures that control access to copyrighted works, including software. However, the DMCA also provides exceptions for certain types of reverse engineering, such as for interoperability purposes.
Ethical Considerations
Beyond the legal risks, reverse engineering also raises ethical considerations. It is important to respect the intellectual property rights of software developers and to use reverse engineering only for legitimate purposes.
Furthermore, it is important to avoid using reverse engineering to create malicious software or to violate licensing agreements.
Mitigation Measures
To mitigate the risks of reverse engineering, it is important to:
- Obtain Authorization: Obtain authorization from the software vendor before reverse engineering any software.
- Comply with Laws and Agreements: Comply with all applicable laws and licensing agreements.
- Use Reverse Engineering Only for Legitimate Purposes: Use reverse engineering only for legitimate purposes, such as interoperability or security auditing.
- Protect Confidential Information: Protect any confidential information that is discovered during reverse engineering.
- Report Vulnerabilities: Report any security vulnerabilities that are discovered to the software vendor.
According to the Electronic Frontier Foundation (EFF), a non-profit organization that defends civil liberties in the digital world, it is important to strike a balance between protecting intellectual property rights and promoting innovation and competition.
9. How Can I Protect My Own Software from Being Cracked?
Protecting your software from being cracked involves a combination of technical measures, legal strategies, and ongoing vigilance. Here’s a breakdown of effective methods:
Strong Encryption
Encryption is the cornerstone of software protection. By encrypting your code, you make it significantly harder for crackers to understand and modify it.
- Code Encryption: Encrypt the entire executable or critical sections of code.
- Data Encryption: Encrypt sensitive data, such as license keys, configuration files, and user data.
- String Encryption: Encrypt strings within your code to prevent easy identification of key functions and logic.
Code Obfuscation
Obfuscation transforms your code into a form that is difficult to read and understand, without changing its functionality.
- Name Obfuscation: Rename variables, functions, and classes to meaningless names.
- Control Flow Obfuscation: Alter the control flow of your code to make it harder to follow.
- Instruction Pattern Transformation: Replace common instruction patterns with equivalent but less obvious patterns.
Anti-Debugging Techniques
Crackers often use debuggers to analyze and modify software. Anti-debugging techniques make it harder for debuggers to attach to your software and analyze its behavior.
- Debugger Detection: Detect the presence of debuggers and terminate the software or alter its behavior.
- Code Integrity Checks: Verify the integrity of the code at runtime to detect any unauthorized modifications.
- Trap Flags: Use trap flags to detect when a debugger is single-stepping through the code.
Licensing and Activation
Robust licensing and activation mechanisms are essential for controlling access to your software.
- Product Keys: Require users to enter a valid product key during installation or activation.
- Online Activation: Verify the license online by connecting to your servers.
- Hardware Locking: Tie the license to specific hardware components, such as the CPU or hard drive.
Watermarking
Watermarking involves embedding hidden markers in your software to identify unauthorized copies.
- Static Watermarking: Embed a unique identifier in the code or data.
- Dynamic Watermarking: Generate a unique identifier at runtime based on user or system information.
Legal Measures
Legal measures are an important complement to technical measures.
- Copyright Protection: Register your software with the copyright office to protect your intellectual property rights.
- End User License Agreement (EULA): Include a EULA that prohibits unauthorized modification, distribution, or reverse engineering.
- Digital Millennium Copyright Act (DMCA): Use the DMCA to take down websites and online services that distribute or promote cracked software.
Regular Updates
Regular updates are essential for fixing security vulnerabilities and staying ahead of crackers.
- Security Patches: Release regular security patches to address known vulnerabilities.
- Code Improvements: Continuously improve the code to make it more resistant to cracking.
- Technological Advancements: Stay up-to-date with the latest anti-cracking technologies and incorporate them into your software.
Monitoring and Vigilance
Monitoring and vigilance are essential for detecting and responding to cracking attempts.
- Online Monitoring: Monitor online forums, websites, and file-sharing networks for cracked versions of your software.
- User Feedback: Encourage users to report suspicious activity or potential vulnerabilities.
- Incident Response Plan: Develop an incident response plan to address cracking attempts quickly and effectively.
According to the Software & Information Industry Association (SIIA), a trade association for the software and digital content industry, a comprehensive approach that combines technical measures, legal strategies, and ongoing vigilance is the most effective way to protect your software from being cracked.
10. Where Can I Learn Advanced Software Repair and Diagnostic Skills?
You can acquire advanced software repair and diagnostic skills through specialized training programs, vocational schools, online courses, and industry certifications. For those in the automotive field, consider programs that focus on remote auto repair and diagnostics, such as those offered at CAR-REMOTE-REPAIR.EDU.VN.
Specialized Training Programs
Specialized training programs provide in-depth instruction and hands-on experience in specific areas of software repair and diagnostics. These programs are often offered by vocational schools, technical colleges, and industry organizations.
Examples of specialized training programs include:
- Remote Auto Repair and Diagnostics: These programs focus on the skills and knowledge needed to diagnose and repair vehicles remotely using specialized software and diagnostic tools. CAR-REMOTE-REPAIR.EDU.VN is a great resource for this. Address: 1700 W Irving Park Rd, Chicago, IL 60613, United States. Whatsapp: +1 (641) 206-8880.
- Software Reverse Engineering: These programs teach students how to analyze software code to understand its functionality and identify vulnerabilities.
- Malware Analysis: These programs focus on the skills and knowledge needed to analyze malware and develop countermeasures.
- Digital Forensics: These programs teach students how to investigate digital crimes and recover evidence from computer systems and networks.
Vocational Schools and Technical Colleges
Vocational schools and technical colleges offer a variety of programs in computer technology, including software repair and diagnostics. These programs typically provide a combination of classroom instruction and hands-on training.
Examples of vocational schools and technical colleges that offer programs in software repair and diagnostics include:
- DeVry University: Offers a variety of programs in computer technology, including software development, network administration, and cybersecurity.
- ITT Technical Institute: Offers programs in electronics technology, computer drafting and design, and information technology.
- Lincoln Tech: Offers programs in automotive technology, including automotive diagnostics and repair.
Online Courses and Tutorials
Online courses and tutorials provide a convenient and affordable way to learn software repair and diagnostic skills. Many online learning platforms offer courses in a variety of computer technology topics.
Examples of online learning platforms that offer courses in software repair and diagnostics include:
- Coursera: Offers courses in computer science, software engineering, and cybersecurity from leading universities and institutions.
- edX: Offers courses in computer science, software engineering, and cybersecurity from top universities around the world.
- Udemy: Offers a variety of courses in computer technology, including software repair and diagnostics.
- LinkedIn Learning: Offers courses in software development, IT infrastructure, and cybersecurity.
Industry Certifications
Industry certifications demonstrate your skills and knowledge in a specific area of software repair and diagnostics. Many organizations offer certifications in a variety of computer technology topics.
Examples of industry certifications include:
- CompTIA A+: A certification that demonstrates your knowledge of computer hardware and software.
- CompTIA Network+: A certification that demonstrates your knowledge of computer networking.
- CompTIA Security+: A certification that demonstrates your knowledge of computer security.
- Certified Ethical Hacker (CEH): A certification that demonstrates your knowledge of ethical hacking and penetration testing.
- Certified Information Systems Security Professional (CISSP): A certification that demonstrates your knowledge of information security.
Hands-On Experience
In addition to formal training and certifications, hands-on experience is essential for developing advanced software repair and diagnostic skills. You can gain hands-on experience by:
- Working on Real-World Projects: Working on real-world projects, such as repairing computers for friends and family or volunteering at a local non-profit organization.
- Participating in Capture the Flag (CTF) Competitions: Participating in CTF competitions, which are online security challenges that test your skills in reverse engineering, cryptography, and other areas of computer security.
- Contributing to Open-Source Projects: Contributing to open-source projects, which can provide valuable experience in software development and debugging.
According to a survey by the Computing Technology Industry Association (CompTIA), employers value certifications and hands-on experience when hiring IT professionals.
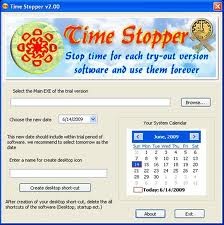 Software Cracking
Software Cracking
FAQ: Converting Trial Software to Full Version
- Is it legal to use a Time Stopper or similar tool to extend the trial period of software?
No, using tools like Time Stopper to extend trial periods is generally illegal and violates the software’s licensing agreement, potentially leading to legal consequences. - What are the ethical considerations when deciding whether to convert trial software to a full version?
Ethically, it’s crucial to respect software developers’ intellectual property and labor by purchasing a license for full use, thus supporting their ability to innovate and improve their products. - How do software licensing models like perpetual, subscription, and open-source differ, and which is best for me?
Perpetual licenses offer a one-time purchase for indefinite use, subscription licenses provide access for recurring fees with updates included, while open-source licenses allow free use, modification, and distribution, making the best choice dependent on your budget, update needs, and long-term use. - Can software license management tools really help me save money?
Yes, software license management tools can significantly cut costs by optimizing license use, ensuring compliance, and preventing unnecessary spending, potentially saving organizations up to 30% on software expenses. - Why is software cracking illegal, and what risks do I face using cracked software?
Software cracking is illegal due to copyright infringement and violation of licensing agreements, and using cracked software exposes you to security risks like malware, lack of updates, instability, and legal repercussions. - What methods do software vendors use to protect their products from piracy?
Software vendors protect their products through a mix of licensing and activation processes, robust copy protection technologies, anti-tamper techniques, and legal enforcement measures to deter unauthorized use. - Is it true that modifying software files can open the door to security vulnerabilities?
Yes, modifying software files can create security holes by introducing bugs, bypassing vital security protocols, and causing compatibility issues, increasing the risk of malware injection and system compromise. - Why is reverse engineering software considered risky, and what are the legal implications?
Reverse engineering is risky as it can breach copyright laws, expose vulnerabilities, and enable malicious software creation, and its legality hinges on adhering to copyright laws and licensing agreements, particularly concerning interoperability purposes. - What steps can I take to effectively protect my own software from being cracked?
You can protect your software by implementing strong encryption, code obfuscation, anti-debugging techniques, robust licensing, watermarking, regular updates, and by actively monitoring for and legally addressing cracking attempts. - Where can I gain advanced software repair and diagnostic skills, especially in remote auto repair?
You can gain advanced skills through specialized training programs, vocational schools, online courses, industry certifications, and hands-on experience, with resources like CAR-REMOTE-REPAIR.EDU.VN offering programs focused on remote auto repair and diagnostics.
Ready to elevate your automotive repair skills and dive into the world of remote diagnostics? Visit CAR-REMOTE-REPAIR.EDU.VN today to explore our comprehensive training programs and cutting-edge services. Contact us now to learn how you can revolutionize your approach to auto repair in the USA! Address: 1700 W Irving Park Rd, Chicago, IL 60613, United States. Whatsapp: +1 (641) 206-8880. Keywords: automotive diagnostics, remote repair training, USA auto services, car diagnostic tools, vehicle maintenance courses.
