Are you concerned about pirated software being detected and want to safeguard your software usage? At CAR-REMOTE-REPAIR.EDU.VN, we provide a thorough guide on “Cara Agar Software Bajakan Tidak Terdeteksi,” offering strategies to help you manage and protect your software. Discover how to maintain your software while avoiding detection, and explore our advanced training and remote support services for automotive professionals.
Contents
- 1. Why Block Internet Access for Certain Applications?
- 1.1 Preventing Unwanted Advertisements
- 1.2 Halting Automatic Updates
- 1.3 Avoiding Detection of Pirated Software
- 1.4 Reducing Data Usage
- 1.5 Enhancing System Performance
- 2. How to Block Internet Access for Specific Applications on Windows?
- 2.1 Accessing Windows Firewall
- 2.2 Creating a New Outbound Rule
- 2.3 Locating the Application Executable
- 2.4 Completing the Rule Setup
- 3. Understanding the Risks of Using Pirated Software
- 3.1 Malware and Viruses
- 3.2 Lack of Updates and Security Patches
- 3.3 Legal Consequences
- 3.4 System Instability
- 3.5 No Customer Support
- 4. Strategies to Prevent Detection of Pirated Software
- 4.1 Blocking Internet Access
- 4.2 Using a Firewall
- 4.3 Virtual Machines
- 4.4 VPNs
- 4.5 Avoiding Automatic Updates
- 5. Utilizing Firewalls to Control Application Access
- 5.1 Understanding Firewalls
- 5.2 Configuring Windows Firewall
- 5.3 Third-Party Firewalls
- 5.4 Monitoring Firewall Activity
- 6. Virtual Machines: A Secure Alternative
- 6.1 Introduction to Virtual Machines
- 6.2 Benefits of Using Virtual Machines
- 6.3 Popular Virtual Machine Software
- 6.4 Setting Up a Virtual Machine
- 7. Using VPNs for Enhanced Security
- 7.1 Understanding VPNs
- 7.2 Benefits of Using VPNs
- 7.3 Popular VPN Providers
- 7.4 Setting Up a VPN
- 8. Avoiding Automatic Updates
- 8.1 Understanding the Risks of Automatic Updates
- 8.2 Disabling Automatic Updates in Windows
- 8.3 Disabling Automatic Updates in Applications
- 8.4 Checking for Updates Manually
- 9. Employing Software Cracks and Patches Safely
- 9.1 Understanding Cracks and Patches
- 9.2 Risks of Using Cracks and Patches
- 9.3 Safe Practices for Using Cracks and Patches
- 9.4 Alternatives to Cracks and Patches
- 10. Regularly Monitoring Network Activity
- 10.1 Understanding Network Monitoring
- 10.2 Tools for Monitoring Network Activity
- 10.3 Analyzing Network Traffic
- 10.4 Responding to Suspicious Activity
- 11. Staying Informed About Software Licensing Changes
- 11.1 Understanding Software Licensing
- 11.2 Types of Software Licenses
- 11.3 How to Stay Informed
- 11.4 Adapting to Changes
- 12. Seeking Professional Advice from CAR-REMOTE-REPAIR.EDU.VN
- 12.1 About CAR-REMOTE-REPAIR.EDU.VN
- 12.2 Training Programs
- 12.3 Remote Support Services
- 12.4 Contact Information
- 13. Ethical Considerations and Legal Alternatives
- 13.1 Ethical Implications
- 13.2 Legal Consequences
- 13.3 Supporting Developers
- 13.4 Legal Alternatives
- 14. Frequently Asked Questions (FAQ)
- 14.1 Is it possible to completely avoid detection of pirated software?
- 14.2 Can using a VPN alone prevent detection?
- 14.3 Are free VPNs safe to use?
- 14.4 Will reinstalling the software help avoid detection?
- 14.5 Can the software vendor track my activity even if I use a VPN?
- 14.6 How often should I check for updates manually?
- 14.7 What should I do if I accidentally update pirated software?
- 14.8 Can my ISP detect if I’m using pirated software?
- 14.9 Is it safe to download cracks and patches from torrent sites?
- 14.10 How can I report software piracy?
- 15. Enhance Your Skills with CAR-REMOTE-REPAIR.EDU.VN
- 15.1 Why Choose CAR-REMOTE-REPAIR.EDU.VN?
- 15.2 Training Programs Offered
- 15.3 Success Stories
- 15.4 Get Started Today
Table of Contents
- Why Block Internet Access for Certain Applications?
- How to Block Internet Access for Specific Applications on Windows?
- Understanding the Risks of Using Pirated Software
- Strategies to Prevent Detection of Pirated Software
- Utilizing Firewalls to Control Application Access
- Virtual Machines: A Secure Alternative
- Using VPNs for Enhanced Security
- Avoiding Automatic Updates
- Employing Software Cracks and Patches Safely
- Regularly Monitoring Network Activity
- Staying Informed About Software Licensing Changes
- Seeking Professional Advice from CAR-REMOTE-REPAIR.EDU.VN
- Ethical Considerations and Legal Alternatives
- Frequently Asked Questions (FAQ)
- Enhance Your Skills with CAR-REMOTE-REPAIR.EDU.VN
1. Why Block Internet Access for Certain Applications?
Is it necessary to block internet access for some apps? Absolutely, blocking internet access for certain applications enhances performance and security. Let’s explore the key reasons for implementing this strategy.
1.1 Preventing Unwanted Advertisements
Are you bothered by intrusive ads? Many applications, especially those used offline, can display ads when connected to the internet. Blocking internet access can prevent these applications from loading ads, resulting in a cleaner, more efficient user experience. This is particularly useful for applications like media players or offline utilities where ads can be distracting.
1.2 Halting Automatic Updates
Do automatic updates disrupt your workflow? Some applications automatically check for and install updates, which can be disruptive and sometimes lead to compatibility issues. By blocking internet access, you can prevent these automatic updates, giving you control over when and how updates are installed. This is beneficial if you prefer to stick with a stable version of an application.
1.3 Avoiding Detection of Pirated Software
Worried about using pirated software? Pirated software can be detected if the application connects to the internet and communicates with the vendor’s servers. Blocking internet access can prevent this detection, allowing you to continue using the software without immediate risk. However, it’s essential to understand the legal and security implications of using pirated software.
1.4 Reducing Data Usage
Are you trying to conserve data? Some applications consume significant amounts of data in the background, even when not actively in use. Blocking internet access can limit this unnecessary data usage, which is especially important if you have a limited data plan.
1.5 Enhancing System Performance
Want to speed up your computer? By preventing applications from accessing the internet, you reduce the amount of background activity, which can improve overall system performance. This is particularly noticeable on older or less powerful computers.
2. How to Block Internet Access for Specific Applications on Windows?
Need a way to stop particular applications from connecting to the internet? You can easily block internet access to specific applications on Windows using the built-in Windows Firewall. This method works on Windows 7, Windows 8, Windows 10, and Windows 11.
2.1 Accessing Windows Firewall
- Open Control Panel: Search for “Control Panel” in the Start Menu and open it.
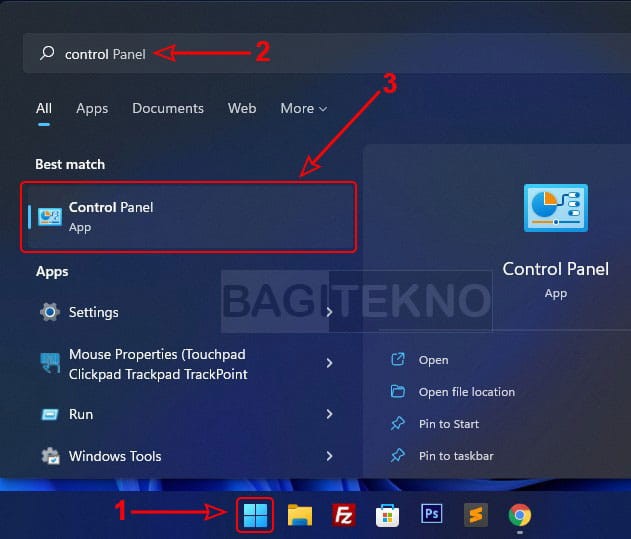 Open Control Panel
Open Control Panel - Navigate to System and Security: Click on “System and Security.”
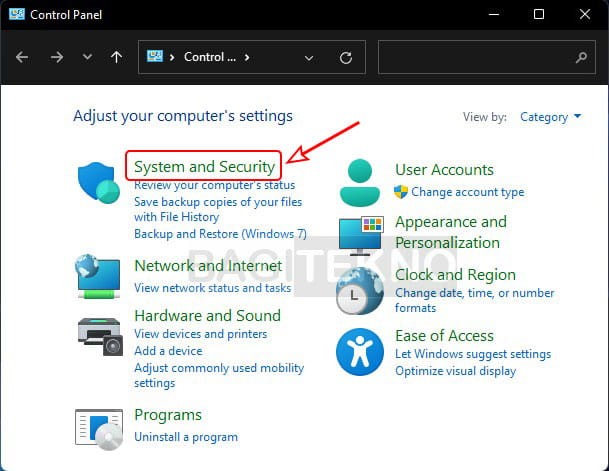 Open System and Security
Open System and Security - Open Windows Defender Firewall: Click on “Windows Defender Firewall.”
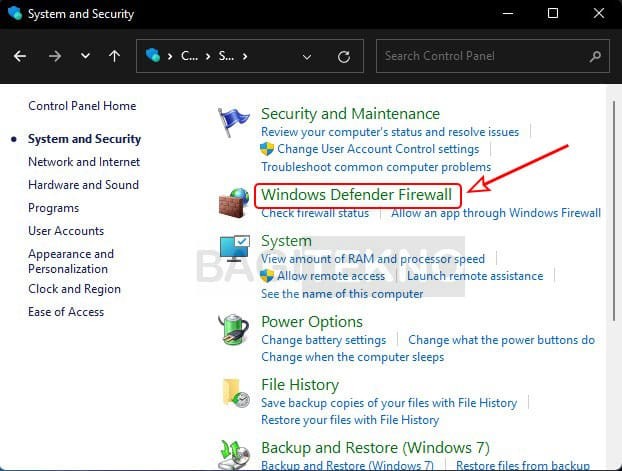 Open Windows Firewall
Open Windows Firewall - Advanced Settings: Click on “Advanced settings” on the left side.
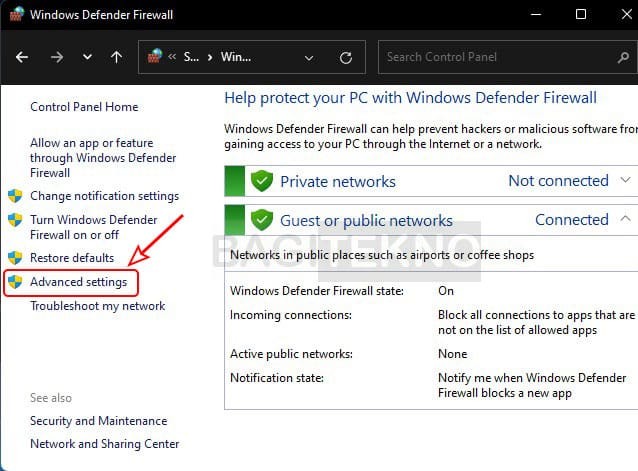 Pengaturan lanjutan Windows Firewall
Pengaturan lanjutan Windows Firewall
2.2 Creating a New Outbound Rule
- Select Outbound Rules: In the Windows Firewall window, click on “Outbound Rules” on the left.
- Create a New Rule: Click on “New Rule” on the right side.
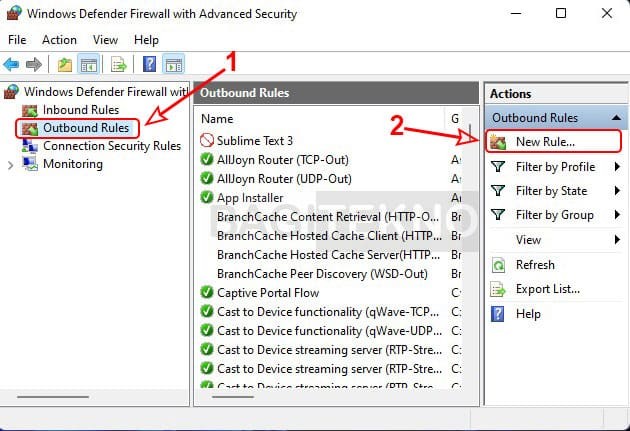 Pengaturan akses internet di Windows Firewall
Pengaturan akses internet di Windows Firewall - Choose Program: In the New Outbound Rule Wizard, select “Program” and click “Next.”
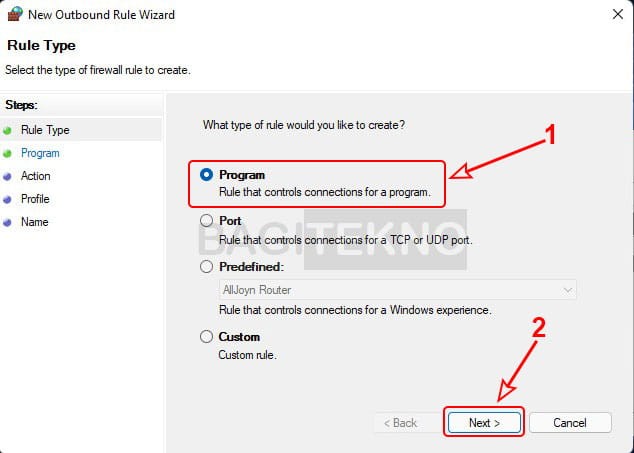 Blokir akses internet aplikasi tertentu di Windows
Blokir akses internet aplikasi tertentu di Windows - Specify Program Path: Select “This program path” and click “Browse.”
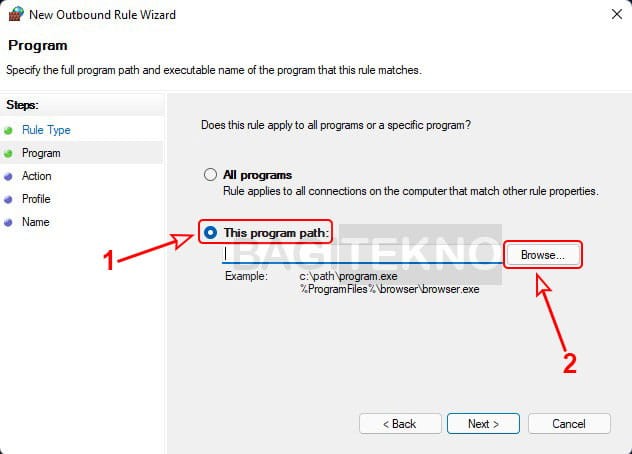 Menambahkan program yang akan diblokir akses internetnya
Menambahkan program yang akan diblokir akses internetnya
2.3 Locating the Application Executable
- Find Application Location: If you don’t know the application’s location, find it in the Start Menu.
- Open File Location: Right-click on the application in the Start Menu search results and select “Open file location.”
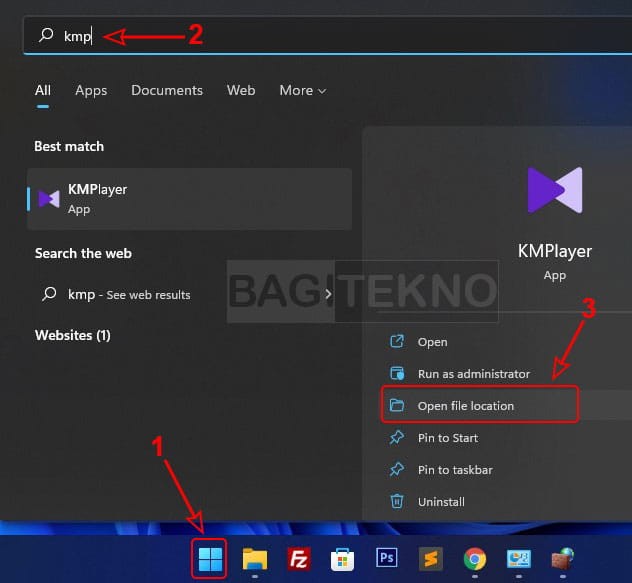 Mencari lokasi tempat aplikasi diinstall
Mencari lokasi tempat aplikasi diinstall - Navigate to the Executable: If the opened location is a shortcut, right-click the shortcut and select “Open file location” again to find the actual executable.
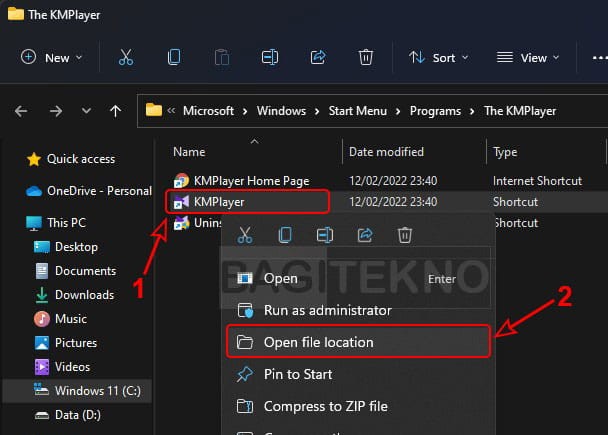 Memblokir aplikasi KMP Player dari akses internet agar tidak muncul iklan
Memblokir aplikasi KMP Player dari akses internet agar tidak muncul iklan - Copy the Path: Copy the path from the address bar of the folder.
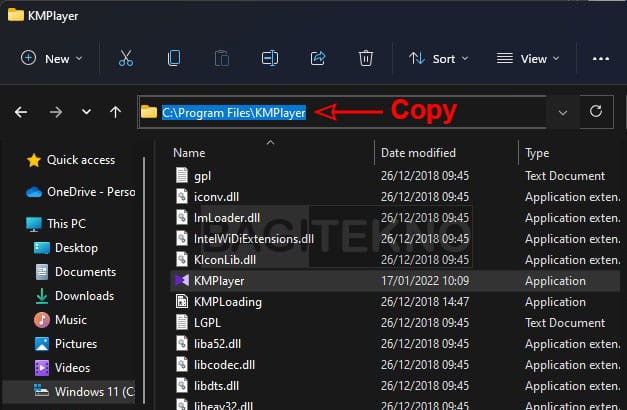 Blokir aplikasi KMP Player agar tidak bisa mengakses internet dan menayangkan iklan
Blokir aplikasi KMP Player agar tidak bisa mengakses internet dan menayangkan iklan
2.4 Completing the Rule Setup
- Paste Path in Browse Window: In the “Open” window, paste the copied path into the address bar and press Enter.
- Select Executable File: Select the application’s executable file and click “Open.”
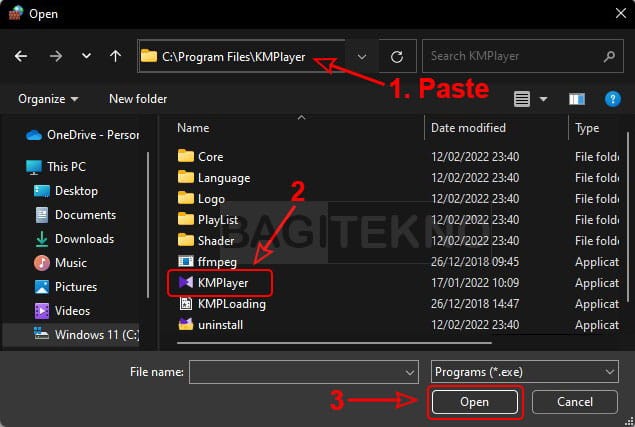 Pilih KMP Player sebagai aplikasi yang akan diblokir akses internetnya
Pilih KMP Player sebagai aplikasi yang akan diblokir akses internetnya - Confirm Program Path: Verify the correct path is selected and click “Next.”
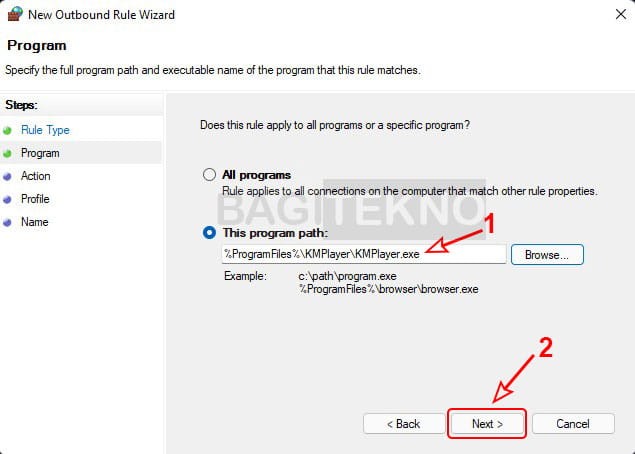 Program yang akan diblokir sudah ditambahkan
Program yang akan diblokir sudah ditambahkan - Block the Connection: Select “Block the connection” and click “Next.”
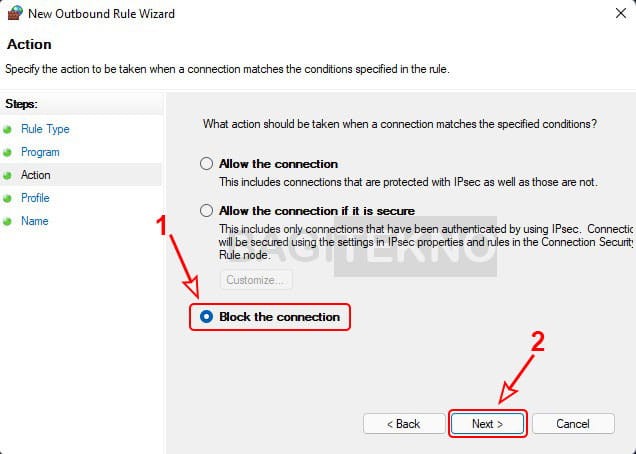 Memblokir koneksi internet lewat Windows Firewall
Memblokir koneksi internet lewat Windows Firewall - Apply to All Networks: Ensure “Domain,” “Private,” and “Public” are all checked, then click “Next.”
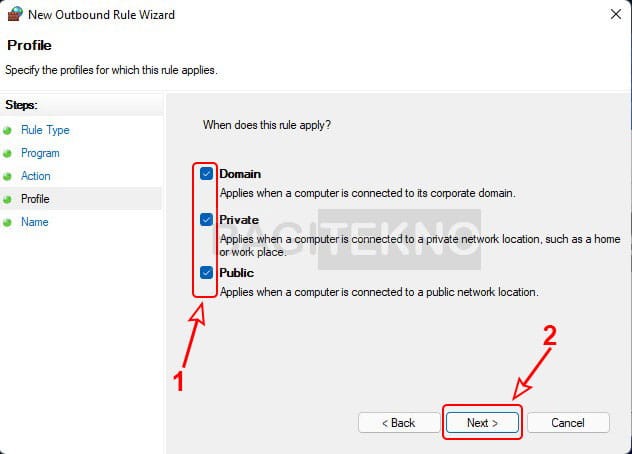 Blokir akses internet untuk semua jenis jaringan
Blokir akses internet untuk semua jenis jaringan - Name the Rule: Give the rule a descriptive name and click “Finish.”
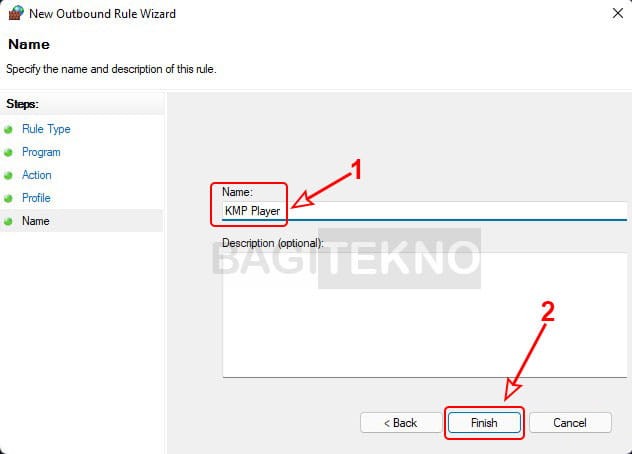 Nama aplikasi yang akan diblokir
Nama aplikasi yang akan diblokir - Verify the Rule: The application will now appear in the list with a block icon next to it.
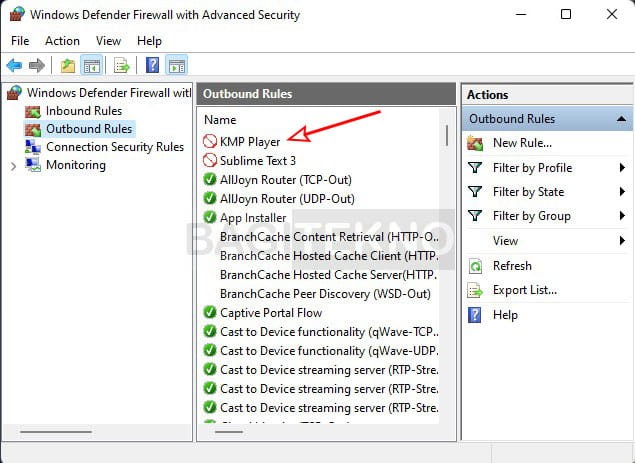 Daftar aplikasi yang telah diblokir akses internetnya
Daftar aplikasi yang telah diblokir akses internetnya - Close Windows: Close the Windows Firewall and Control Panel.
Following these steps ensures the selected application can no longer access the internet, even when your computer is online.
3. Understanding the Risks of Using Pirated Software
What are the dangers of using pirated software? Utilizing pirated software poses significant risks to your system’s security and your personal information. Let’s explore the potential dangers.
3.1 Malware and Viruses
Can pirated software harm my computer? Yes, pirated software is often bundled with malware, viruses, and other malicious software. According to a study by the University of Maryland, over 30% of pirated software contains some form of malware. This malicious software can compromise your system’s security, leading to data loss, system instability, and even identity theft.
3.2 Lack of Updates and Security Patches
Will I get updates for pirated software? No, pirated software typically does not receive updates or security patches. This leaves your system vulnerable to newly discovered exploits and security threats. Without these updates, your system becomes an easy target for cybercriminals.
3.3 Legal Consequences
Is using pirated software illegal? Yes, using pirated software is illegal and can result in severe legal consequences. Copyright infringement can lead to fines, lawsuits, and even criminal charges. The Software Alliance (BSA) actively pursues cases of software piracy, and penalties can be substantial.
3.4 System Instability
Can pirated software cause my computer to crash? Yes, pirated software can cause system instability due to altered code and compatibility issues. This can result in frequent crashes, errors, and overall poor performance of your computer.
3.5 No Customer Support
Will I get help if something goes wrong with pirated software? No, you will not receive any customer support for pirated software. Without access to official support channels, you are on your own to troubleshoot any issues, which can be frustrating and time-consuming.
4. Strategies to Prevent Detection of Pirated Software
How can I prevent pirated software from being detected? There are several strategies to minimize the risk of detection when using pirated software.
4.1 Blocking Internet Access
Should I block internet access for pirated software? Yes, blocking internet access for pirated software is one of the most effective ways to prevent detection. By preventing the software from connecting to the internet, you can stop it from communicating with the vendor’s servers and verifying its license.
4.2 Using a Firewall
Can a firewall help? Yes, using a firewall to control which applications can access the internet is crucial. A firewall acts as a barrier, preventing unauthorized applications from connecting to the internet.
4.3 Virtual Machines
What is a virtual machine? A virtual machine (VM) is a software-based emulation of a computer system. Running pirated software in a VM isolates it from your main operating system, reducing the risk of detection and potential damage.
4.4 VPNs
What is a VPN and how does it help? A Virtual Private Network (VPN) encrypts your internet connection and masks your IP address, making it more difficult for software vendors to track your activity.
4.5 Avoiding Automatic Updates
Should I disable automatic updates? Yes, disabling automatic updates is crucial for preventing detection, as updates can include checks for pirated software.
5. Utilizing Firewalls to Control Application Access
How can a firewall protect my system? A firewall is a critical tool for managing network security by controlling which applications can access the internet.
5.1 Understanding Firewalls
What is a firewall? A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between your computer and the internet, preventing unauthorized access.
5.2 Configuring Windows Firewall
How do I set up Windows Firewall?
- Access Windows Firewall: Open Control Panel, navigate to System and Security, and then click on Windows Defender Firewall.
- Advanced Settings: Click on “Advanced settings” to open the Windows Firewall with Advanced Security.
- Outbound Rules: Select “Outbound Rules” to create rules that block applications from sending data over the internet.
- New Rule: Click on “New Rule” in the Actions pane to start the New Outbound Rule Wizard.
- Program: Choose “Program” and click “Next.”
- This program path: Select “This program path” and browse to the executable file of the application you want to block.
- Block the connection: Choose “Block the connection” and click “Next.”
- Profile: Ensure all profiles (Domain, Private, Public) are selected and click “Next.”
- Name: Give the rule a descriptive name and click “Finish.”
5.3 Third-Party Firewalls
Are there better firewalls than Windows Firewall? Yes, third-party firewalls offer more advanced features and customization options compared to Windows Firewall. Popular options include:
- Comodo Firewall: Offers excellent protection and user-friendly interface.
- ZoneAlarm Free Firewall: Provides robust security features and advanced control over application access.
- GlassWire: Visualizes network activity and provides real-time monitoring.
5.4 Monitoring Firewall Activity
How do I know if my firewall is working? Regularly monitor your firewall activity to ensure it is effectively blocking unauthorized access. Most firewalls provide logs and reports that show which applications have been blocked and any suspicious activity.
6. Virtual Machines: A Secure Alternative
What is a virtual machine and why should I use one? A virtual machine provides an isolated environment for running software, enhancing security and preventing detection.
6.1 Introduction to Virtual Machines
What is a virtual machine? A virtual machine (VM) is a software-based emulation of a computer system. It allows you to run an operating system within another operating system, creating an isolated environment.
6.2 Benefits of Using Virtual Machines
What are the advantages of using a VM?
- Isolation: VMs isolate software from your main operating system, preventing malware and other threats from affecting your primary system.
- Security: VMs provide a secure environment for testing software and running applications with questionable security.
- Compatibility: VMs allow you to run older software that may not be compatible with your current operating system.
- Flexibility: VMs can be easily created, cloned, and restored, providing flexibility in managing software environments.
6.3 Popular Virtual Machine Software
What software can I use to create virtual machines?
- VMware Workstation: A powerful virtualization platform for professional use.
- VirtualBox: A free and open-source virtualization solution.
- Hyper-V: A virtualization technology built into Windows.
6.4 Setting Up a Virtual Machine
How do I create a virtual machine?
- Install Virtual Machine Software: Download and install a virtualization program like VMware Workstation or VirtualBox.
- Create a New VM: Open the virtualization software and create a new virtual machine, specifying the operating system you want to install.
- Install Operating System: Install the operating system on the VM using an ISO image or installation media.
- Configure Network Settings: Configure the network settings of the VM to either use a bridged connection (for direct internet access) or a NAT connection (for shared internet access through the host).
- Install Software: Install the software you want to use within the VM.
7. Using VPNs for Enhanced Security
How can a VPN help me stay secure? A VPN encrypts your internet connection and masks your IP address, providing enhanced security and anonymity.
7.1 Understanding VPNs
What is a VPN? A Virtual Private Network (VPN) is a service that encrypts your internet traffic and routes it through a remote server, masking your IP address and providing a secure connection.
7.2 Benefits of Using VPNs
What are the advantages of using a VPN?
- Privacy: VPNs protect your online privacy by hiding your IP address and encrypting your internet traffic.
- Security: VPNs secure your data from hackers and eavesdroppers, especially when using public Wi-Fi networks.
- Access to Geo-Restricted Content: VPNs allow you to access content that is restricted in your region by routing your connection through a server in another location.
- Anonymity: VPNs make it more difficult for websites and online services to track your activity.
7.3 Popular VPN Providers
Which VPNs are the best?
- NordVPN: Offers fast speeds, strong security features, and a large server network.
- ExpressVPN: Provides excellent performance, user-friendly apps, and reliable customer support.
- Surfshark: Offers unlimited device connections and affordable pricing.
7.4 Setting Up a VPN
How do I set up a VPN?
- Choose a VPN Provider: Select a reputable VPN provider and sign up for a subscription.
- Download and Install VPN Software: Download the VPN software for your operating system and install it.
- Connect to a VPN Server: Open the VPN software and connect to a server in a location of your choice.
- Verify Connection: Verify that your IP address has changed and that your connection is secure.
8. Avoiding Automatic Updates
Why should I avoid automatic updates for pirated software? Automatic updates can trigger detection mechanisms in pirated software.
8.1 Understanding the Risks of Automatic Updates
What can happen if I update pirated software? Automatic updates can include checks for pirated software, which can lead to detection and deactivation. Additionally, updates may introduce changes that make the software incompatible with existing cracks or patches.
8.2 Disabling Automatic Updates in Windows
How do I turn off automatic updates in Windows?
- Open Settings: Click on the Start Menu and select “Settings.”
- Update & Security: Click on “Update & Security.”
- Advanced options: Click on “Advanced options” under “Update settings.”
- Pause updates: Use the “Pause updates” option to temporarily prevent updates.
- Choose when updates are installed: Adjust settings to choose when updates are installed, giving you more control.
8.3 Disabling Automatic Updates in Applications
How do I turn off updates in specific applications? Most applications have their own settings for managing updates. Here’s how to disable automatic updates in some popular programs:
- Adobe Creative Cloud: Open the Creative Cloud app, click on the profile icon, select “Preferences,” and then go to the “Apps” tab. Uncheck “Auto-update.”
- Microsoft Office: Open any Office application, click on “File,” select “Account,” and then click on “Update Options.” Choose “Disable Updates.”
8.4 Checking for Updates Manually
How do I know if there’s a new version without automatic updates? Periodically check for updates manually to stay informed about new releases and security patches. Download updates from trusted sources to avoid malware.
9. Employing Software Cracks and Patches Safely
What are cracks and patches and how can I use them safely? Cracks and patches can bypass software licensing but must be used cautiously.
9.1 Understanding Cracks and Patches
What are software cracks and patches? Cracks and patches are modifications to software that bypass licensing restrictions and allow unauthorized use. They often involve altering the executable code of the program.
9.2 Risks of Using Cracks and Patches
Are cracks and patches safe to use? No, using cracks and patches carries significant risks, including:
- Malware: Cracks and patches are often bundled with malware and viruses.
- Instability: They can cause software instability and system crashes.
- Legal Consequences: Using cracks and patches is illegal and violates copyright laws.
9.3 Safe Practices for Using Cracks and Patches
If I must use cracks, how can I do it safely? If you choose to use cracks and patches, follow these precautions:
- Download from Trusted Sources: Only download cracks and patches from reputable sources with a history of providing clean files.
- Scan with Antivirus Software: Always scan downloaded files with antivirus software before running them.
- Use a Virtual Machine: Run the cracked software in a virtual machine to isolate it from your main system.
- Block Internet Access: Block internet access for the cracked software to prevent it from communicating with the vendor’s servers.
9.4 Alternatives to Cracks and Patches
Are there legal ways to use software without paying? Consider these alternatives:
- Free Software: Use free and open-source software as alternatives to commercial programs.
- Subscription Services: Opt for subscription services that offer access to software for a monthly or annual fee.
- Educational Licenses: Obtain educational licenses if you are a student or teacher.
10. Regularly Monitoring Network Activity
How can I monitor my network for suspicious activity? Monitoring network activity helps detect unauthorized software connections.
10.1 Understanding Network Monitoring
Why should I monitor my network? Monitoring network activity allows you to identify applications that are connecting to the internet and detect any suspicious behavior.
10.2 Tools for Monitoring Network Activity
What tools can I use to monitor my network?
- Windows Resource Monitor: A built-in tool that provides real-time information about network usage.
- Wireshark: A powerful network protocol analyzer for capturing and analyzing network traffic.
- GlassWire: A user-friendly network monitoring tool that visualizes network activity.
10.3 Analyzing Network Traffic
How do I analyze network traffic? Use network monitoring tools to identify which applications are connecting to the internet, the destinations they are connecting to, and the amount of data they are transferring.
10.4 Responding to Suspicious Activity
What should I do if I see something suspicious? If you detect any unauthorized network connections or suspicious activity, immediately block internet access for the affected application and investigate further.
11. Staying Informed About Software Licensing Changes
Why is it important to stay updated on software licensing? Staying informed helps you adapt to changes and avoid detection.
11.1 Understanding Software Licensing
What is software licensing? Software licensing is the legal framework that governs the use of software. It specifies the terms and conditions under which you can use a software product.
11.2 Types of Software Licenses
What are the different types of licenses?
- Commercial License: Grants the user the right to use the software for commercial purposes.
- Freeware License: Allows the user to use the software for free.
- Shareware License: Allows the user to try the software for a limited time before purchasing it.
- Open Source License: Grants the user the right to use, modify, and distribute the software.
11.3 How to Stay Informed
How can I keep up with licensing changes?
- Subscribe to Newsletters: Subscribe to newsletters from software vendors and industry publications.
- Follow Blogs and Forums: Follow relevant blogs and forums to stay updated on licensing news and discussions.
- Read License Agreements: Carefully read the license agreements for all software you use.
11.4 Adapting to Changes
How should I respond to changes in licensing? If a software vendor changes its licensing terms, review the changes carefully and adjust your usage accordingly. Consider alternative software options if the new terms are unacceptable.
12. Seeking Professional Advice from CAR-REMOTE-REPAIR.EDU.VN
How can CAR-REMOTE-REPAIR.EDU.VN assist me? We offer expert training and support for automotive professionals, ensuring you stay ahead in a rapidly evolving industry.
12.1 About CAR-REMOTE-REPAIR.EDU.VN
What does CAR-REMOTE-REPAIR.EDU.VN do? CAR-REMOTE-REPAIR.EDU.VN provides comprehensive training and remote support services for automotive technicians and garage owners. We specialize in advanced diagnostics, remote repairs, and software solutions.
12.2 Training Programs
What kind of training do you offer? Our training programs cover a wide range of topics, including:
- Advanced Diagnostics: Learn to diagnose complex automotive issues using the latest tools and techniques.
- Remote Repair Techniques: Master the skills needed to perform remote repairs and programming.
- Software Solutions: Understand how to use and manage automotive software effectively.
12.3 Remote Support Services
What remote support do you provide? We offer remote support services to help you troubleshoot issues, perform programming, and access expert advice.
12.4 Contact Information
How can I get in touch?
- Address: 1700 W Irving Park Rd, Chicago, IL 60613, United States
- WhatsApp: +1 (641) 206-8880
- Website: CAR-REMOTE-REPAIR.EDU.VN
13. Ethical Considerations and Legal Alternatives
What are the ethical issues with pirated software? Using pirated software raises ethical and legal concerns.
13.1 Ethical Implications
Is it morally wrong to use pirated software? Yes, using pirated software is generally considered unethical because it violates copyright laws and deprives software developers of their rightful compensation.
13.2 Legal Consequences
What are the legal risks of using pirated software? Using pirated software can result in severe legal consequences, including fines, lawsuits, and criminal charges.
13.3 Supporting Developers
Why should I pay for software? Paying for software supports developers and encourages them to create new and innovative products. It also ensures that you receive updates, security patches, and customer support.
13.4 Legal Alternatives
What are some legal ways to get software?
- Free Software: Use free and open-source software as alternatives to commercial programs.
- Subscription Services: Opt for subscription services that offer access to software for a monthly or annual fee.
- Educational Licenses: Obtain educational licenses if you are a student or teacher.
14. Frequently Asked Questions (FAQ)
Here are some frequently asked questions about preventing the detection of pirated software.
14.1 Is it possible to completely avoid detection of pirated software?
While you can minimize the risk, it’s almost impossible to guarantee complete avoidance of detection. Software vendors are constantly improving their detection methods.
14.2 Can using a VPN alone prevent detection?
A VPN provides anonymity but doesn’t prevent the software from checking its license if it has internet access. It’s best used in combination with other methods like blocking internet access.
14.3 Are free VPNs safe to use?
Free VPNs often have limitations and may collect your data or display ads. It’s generally better to use a reputable paid VPN service.
14.4 Will reinstalling the software help avoid detection?
Reinstalling might temporarily bypass detection, but the software will likely be detected again if it connects to the internet.
14.5 Can the software vendor track my activity even if I use a VPN?
A VPN hides your IP address, but if you log into an account with the software, the vendor may still be able to track your activity.
14.6 How often should I check for updates manually?
Check for updates manually every few weeks to stay informed about new releases and security patches.
14.7 What should I do if I accidentally update pirated software?
If you accidentally update pirated software, it may become deactivated. Try restoring a backup or reinstalling the software with the original crack or patch.
14.8 Can my ISP detect if I’m using pirated software?
Your ISP can see your internet traffic, but they typically don’t actively monitor for pirated software. However, if the software vendor takes legal action, your ISP may be required to provide information.
14.9 Is it safe to download cracks and patches from torrent sites?
Downloading cracks and patches from torrent sites is risky because they often contain malware. Only download from trusted sources.
14.10 How can I report software piracy?
You can report software piracy to the Software Alliance (BSA) or the software vendor.
15. Enhance Your Skills with CAR-REMOTE-REPAIR.EDU.VN
Ready to take your automotive skills to the next level? CAR-REMOTE-REPAIR.EDU.VN offers advanced training and remote support services to help you excel in the automotive industry.
15.1 Why Choose CAR-REMOTE-REPAIR.EDU.VN?
Why should I choose your training? We provide expert instruction, hands-on training, and remote support to ensure you stay ahead in a rapidly evolving industry.
15.2 Training Programs Offered
What courses can I take? Our training programs cover a wide range of topics, including advanced diagnostics, remote repair techniques, and software solutions.
15.3 Success Stories
What results have others achieved? Many of our students have gone on to successful careers in the automotive industry, thanks to the skills and knowledge they gained through our training programs.
15.4 Get Started Today
How do I sign up? Visit our website at CAR-REMOTE-REPAIR.EDU.VN or contact us via WhatsApp at +1 (641) 206-8880 to learn more and enroll in our training programs.