Blocking software with Windows 10 Firewall is a crucial security measure, especially in the auto repair industry where sensitive data and specialized software are often involved. This comprehensive guide, brought to you by CAR-REMOTE-REPAIR.EDU.VN, will walk you through the process, providing detailed steps and troubleshooting tips to ensure your systems are protected. Master firewall management and secure your network today with effective software restriction techniques.
Contents
- 1. Why Block Software with Windows 10 Firewall?
- 1.1 What are the benefits of blocking software?
- 1.2 How does it improve network security?
- 2. Who Needs to Know How to Block Software?
- 2.1 Why is this important for auto repair technicians?
- 2.2 What are the benefits for garage owners and managers?
- 2.3 How can it help automotive educators?
- 3. Identifying Your Intent: Why are you here?
- 3.1 Are you trying to prevent a specific program from accessing the internet?
- 3.2 Do you need to block a program from receiving incoming connections?
- 3.3 Are you troubleshooting network issues and suspect a specific program is the cause?
- 4. Step-by-Step Guide: Blocking Software in Windows 10 Firewall
- 4.1 Accessing Windows Defender Firewall
- 4.2 Launching Advanced Security Settings
- 4.3 Creating an Outbound Rule
- 4.4 Selecting the Program
- 4.5 Choosing the Action
- 4.6 Specifying the Profile
- 4.7 Naming and Finishing the Rule
- 4.8 Creating an Inbound Rule (If Necessary)
- 5. Alternative Methods to Block Software
- 5.1 Using Group Policy (for Domain Networks)
- 5.2 Third-Party Firewall Software
- 6. Troubleshooting Common Issues
- 6.1 Program Still Accessing the Internet
- 6.2 Firewall Blocking Essential Programs
- 6.3 Unable to Locate the Program’s Executable File
- 6.4 Conflicts with Antivirus Software
- 7. Practical Applications in Auto Repair
- 7.1 Securing Diagnostic Tools
- 7.2 Preventing Unauthorized Access to Customer Data
- 7.3 Controlling Software Usage in the Workshop
- 8. Best Practices for Firewall Management
- 8.1 Regularly Reviewing Firewall Rules
- 8.2 Keeping the Firewall Software Updated
- 8.3 Monitoring Firewall Logs
- 9. CAR-REMOTE-REPAIR.EDU.VN: Enhancing Your Skills
- 9.1 Our Training Programs
- 9.2 Our Support Services
- 10. Real-World Examples
- 10.1 Case Study 1: Preventing a Ransomware Attack
- 10.2 Case Study 2: Securing Customer Data
- 10.3 Case Study 3: Controlling Software Usage
- 11. The Future of Firewall Management
- 11.1 AI and Machine Learning
- 11.2 Cloud-Based Firewalls
- 11.3 Integration with Other Security Tools
- 12. Frequently Asked Questions (FAQ)
- 12.1 Can I block system programs with the firewall?
- 12.2 How do I know if a program is safe to allow through the firewall?
- 12.3 What should I do if I accidentally block an essential program?
- 12.4 Can blocking a program slow down my computer?
- 12.5 Is it possible to block a program temporarily?
- 12.6 How often should I review my firewall rules?
- 12.7 What is the difference between inbound and outbound rules?
- 12.8 Can I use the Windows 10 Firewall to block websites?
- 12.9 Does blocking a program prevent it from being installed?
- 12.10 What are the best practices for naming firewall rules?
- 13. Take Action Today!
1. Why Block Software with Windows 10 Firewall?
Blocking software with the Windows 10 Firewall is a proactive security measure that can protect your systems in several ways. According to cybersecurity experts, firewalls are essential for maintaining network integrity.
1.1 What are the benefits of blocking software?
Blocking software can offer several advantages, including:
- Resource Consumption: Limits the resources a program can consume, preventing performance issues.
- Internet Access Control: Manages which programs can access the internet, reducing the risk of unauthorized data transmission.
- Malicious Access Prevention: Blocks inbound access from malicious sources, safeguarding your system from potential threats.
- Outbound Access Restriction: Prevents installed apps from sending data without your permission, enhancing privacy and security.
1.2 How does it improve network security?
By blocking unauthorized or suspicious software, you reduce the attack surface available to cybercriminals. The Windows 10 Firewall acts as a barrier, preventing malicious programs from communicating with external servers or other devices on your network. This is particularly important in the auto repair industry, where diagnostic tools and customer data need to be protected.
2. Who Needs to Know How to Block Software?
Understanding how to block software is vital for various professionals in the auto repair industry, each with unique needs and challenges.
2.1 Why is this important for auto repair technicians?
Auto repair technicians often use specialized software for diagnostics, programming, and accessing repair manuals. Knowing how to block unauthorized software can prevent malware infections and protect sensitive customer data. Additionally, it ensures that only trusted applications have access to the internet, reducing the risk of data breaches.
2.2 What are the benefits for garage owners and managers?
Garage owners and managers are responsible for maintaining a secure network environment for their business. Blocking unnecessary or potentially harmful software can help prevent disruptions, protect customer information, and maintain the integrity of their operations. It also ensures compliance with data protection regulations.
2.3 How can it help automotive educators?
Automotive educators can use firewall settings to create a controlled environment for students to learn about software applications without compromising network security. By blocking certain programs, educators can prevent students from accidentally installing malicious software or accessing unauthorized websites.
3. Identifying Your Intent: Why are you here?
Before diving into the technical steps, it’s important to understand your primary goal. Identifying your intent ensures that the solutions provided are tailored to your specific needs.
3.1 Are you trying to prevent a specific program from accessing the internet?
If your goal is to prevent a particular program from accessing the internet, you’ll need to create outbound rules in the Windows 10 Firewall. This is useful for software that doesn’t require internet access or programs that you suspect may be transmitting data without your consent.
3.2 Do you need to block a program from receiving incoming connections?
Blocking incoming connections is crucial for preventing unauthorized access to your system. This is particularly important for programs that listen for incoming connections, such as remote access tools or file-sharing applications.
3.3 Are you troubleshooting network issues and suspect a specific program is the cause?
Sometimes, network issues can be traced back to a specific program causing conflicts or consuming excessive bandwidth. Blocking the program temporarily can help you diagnose the problem and determine whether it’s the root cause.
4. Step-by-Step Guide: Blocking Software in Windows 10 Firewall
This section provides a detailed, step-by-step guide on how to block software using the Windows 10 Firewall.
4.1 Accessing Windows Defender Firewall
There are several ways to access the Windows Defender Firewall. Here’s how:
- Using the Control Panel:
- Open the Control Panel.
- Click on System and Security.
- Select Windows Defender Firewall.
- Using the Search Bar:
- Type “Windows Defender Firewall” in the search bar.
- Click on Windows Defender Firewall in the search results.
- Using the Run Command:
- Press Windows Key + R to open the Run dialog.
- Type
control firewall.cpland press Enter.
4.2 Launching Advanced Security Settings
To access the advanced settings, follow these steps:
- In the Windows Defender Firewall window, click on Advanced settings in the left pane.
- This will open the Windows Defender Firewall with Advanced Security console.
4.3 Creating an Outbound Rule
Outbound rules control the outgoing traffic from your machine. Here’s how to create one:
- In the left pane, select Outbound Rules.
- In the right pane, under Actions, click on New Rule….
- The New Outbound Rule Wizard will open.
4.4 Selecting the Program
- In the Rule Type step, select Program and click Next.
- In the Program step, select This program path: and click Browse….
- Navigate to the program’s executable (.exe) file and select it.
- Click Next.
4.5 Choosing the Action
- In the Action step, select Block the connection and click Next.
- This ensures that the program will not be able to make any outbound connections.
4.6 Specifying the Profile
- In the Profile step, select the profiles to which the rule should apply. You can choose Domain, Private, and Public.
- Click Next.
4.7 Naming and Finishing the Rule
- In the Name step, enter a descriptive name for the rule (e.g., “Block [Program Name] Outbound”).
- You can also add a description for future reference.
- Click Finish.
4.8 Creating an Inbound Rule (If Necessary)
If you also need to block incoming connections to the program, follow these steps:
- In the left pane, select Inbound Rules.
- In the right pane, under Actions, click on New Rule….
- Follow the same steps as above, but in the Action step, select Block the connection.
- Name the rule appropriately (e.g., “Block [Program Name] Inbound”).
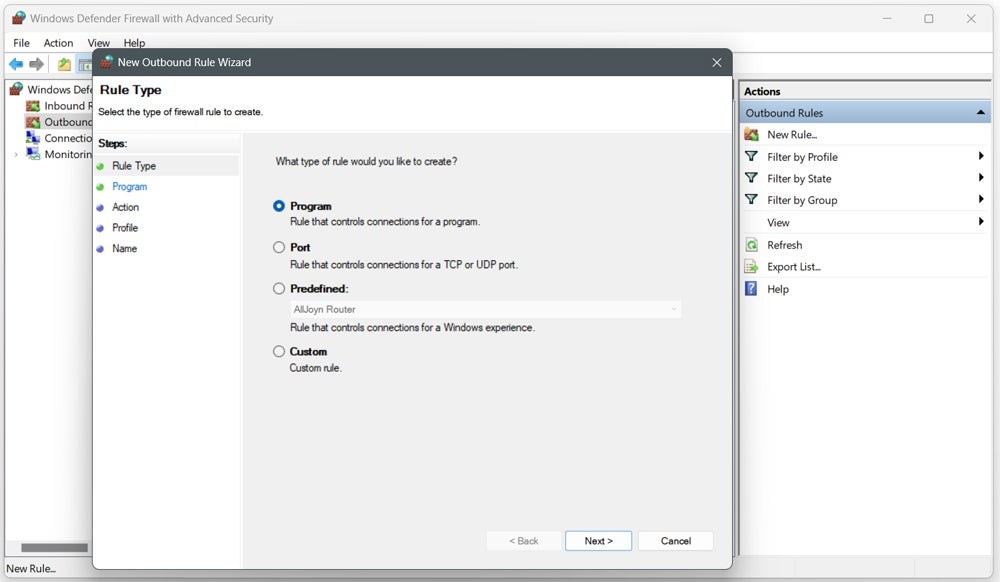 Selecting a rule type on the New Outbound Rule Wizard window.
Selecting a rule type on the New Outbound Rule Wizard window.
5. Alternative Methods to Block Software
While the Windows 10 Firewall is a robust tool, there are alternative methods you can use to block software, depending on your specific needs.
5.1 Using Group Policy (for Domain Networks)
If you’re managing a domain network, you can use Group Policy to block software for multiple users and computers.
- Open the Group Policy Management Console (GPMC).
- Navigate to the appropriate Group Policy Object (GPO).
- Edit the GPO.
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Software Restriction Policies.
- If no software restriction policies are defined, right-click and select New Software Restriction Policies.
- Right-click on Additional Rules and select New Path Rule.
- Enter the path to the program’s executable file and select Disallowed.
- Click OK.
- Update the Group Policy on the client computers by running
gpupdate /forcein the Command Prompt.
5.2 Third-Party Firewall Software
Several third-party firewall software options offer advanced features and more granular control over network traffic. Some popular options include:
- Comodo Firewall: Offers advanced protection with features like application control and behavior analysis.
- ZoneAlarm Free Firewall: Provides a user-friendly interface and robust protection against inbound and outbound threats.
- GlassWire: Visualizes network activity and provides detailed information about which applications are accessing the internet.
6. Troubleshooting Common Issues
Blocking software isn’t always straightforward. Here are some common issues you might encounter and how to troubleshoot them.
6.1 Program Still Accessing the Internet
If a program is still accessing the internet after you’ve created a blocking rule, consider the following:
- Check the Rule: Ensure that the rule is enabled and correctly configured.
- Multiple Executables: Some programs have multiple executable files. Make sure you’ve blocked all relevant files.
- Conflicting Rules: Check for conflicting rules that might be allowing the program to connect.
- Restart the Program: Restart the program to ensure that the new rule is applied.
6.2 Firewall Blocking Essential Programs
If the firewall is blocking essential programs, you’ll need to create an exception rule to allow them to communicate.
- Follow the steps to create a new outbound or inbound rule.
- In the Action step, select Allow the connection.
- Configure the rule to apply only to the specific program and network profiles.
6.3 Unable to Locate the Program’s Executable File
If you’re having trouble locating the program’s executable file, try the following:
- Check the Installation Directory: Look in the program’s installation directory (usually in
C:Program FilesorC:Program Files (x86)). - Use Task Manager: Open Task Manager, find the program in the Processes tab, right-click, and select Open File Location.
- Search the System: Use the Windows search feature to search for the program’s name or executable file.
6.4 Conflicts with Antivirus Software
Sometimes, antivirus software can interfere with firewall rules. To resolve this:
- Check Antivirus Settings: Review your antivirus software’s settings to see if it’s blocking or interfering with the firewall.
- Create Exceptions: Add the program to the antivirus software’s exception list.
- Disable Antivirus Temporarily: Temporarily disable the antivirus software to see if it’s the cause of the issue.
7. Practical Applications in Auto Repair
In the auto repair industry, knowing how to block software can be particularly useful in several scenarios.
7.1 Securing Diagnostic Tools
Diagnostic tools often require internet access for updates and accessing online databases. However, they can also be vulnerable to malware. Blocking unnecessary connections can help secure these tools.
- Allowing Specific Connections: Allow only the specific connections required for updates and database access.
- Blocking Unknown Connections: Block any unknown or suspicious connections.
- Regularly Updating Software: Keep the diagnostic tools updated with the latest security patches.
7.2 Preventing Unauthorized Access to Customer Data
Customer data is sensitive and must be protected. Blocking unauthorized software can prevent data breaches.
- Limiting Access: Limit access to customer data to only authorized personnel and software.
- Blocking File-Sharing Applications: Block file-sharing applications that could be used to exfiltrate data.
- Monitoring Network Traffic: Monitor network traffic for suspicious activity.
7.3 Controlling Software Usage in the Workshop
In a workshop environment, it’s important to control which software is being used to prevent unauthorized access and ensure compliance with licensing agreements.
- Blocking Unnecessary Software: Block any software that is not required for the operation of the workshop.
- Enforcing Software Policies: Enforce software policies through Group Policy or other management tools.
- Regular Audits: Conduct regular audits to ensure compliance with software policies.
8. Best Practices for Firewall Management
Effective firewall management is an ongoing process. Here are some best practices to follow:
8.1 Regularly Reviewing Firewall Rules
Firewall rules should be reviewed regularly to ensure that they are still relevant and effective.
- Removing Obsolete Rules: Remove any rules that are no longer needed.
- Updating Existing Rules: Update existing rules to reflect changes in software or network configurations.
- Auditing Rules: Audit the firewall rules to ensure that they are configured correctly and are not causing any unintended consequences.
8.2 Keeping the Firewall Software Updated
Keeping the firewall software updated is essential for protecting against the latest threats.
- Enabling Automatic Updates: Enable automatic updates to ensure that the firewall is always up-to-date.
- Monitoring Updates: Monitor updates to ensure that they are installed correctly and are not causing any issues.
- Testing Updates: Test updates in a non-production environment before deploying them to the production network.
8.3 Monitoring Firewall Logs
Firewall logs can provide valuable insights into network activity and potential security threats.
- Enabling Logging: Enable logging to capture detailed information about network traffic.
- Analyzing Logs: Analyze the logs to identify suspicious activity.
- Automating Log Analysis: Automate log analysis using security information and event management (SIEM) tools.
 Confirmation window on macOS.
Confirmation window on macOS.
9. CAR-REMOTE-REPAIR.EDU.VN: Enhancing Your Skills
At CAR-REMOTE-REPAIR.EDU.VN, we understand the challenges faced by auto repair professionals in today’s digital landscape. That’s why we offer specialized training and support to help you stay ahead of the curve.
9.1 Our Training Programs
Our training programs are designed to provide you with the skills and knowledge you need to excel in the auto repair industry.
- Remote Diagnostics: Learn how to diagnose and repair vehicles remotely using the latest tools and techniques.
- Cybersecurity for Auto Repair: Understand the cybersecurity threats facing the auto repair industry and how to protect your systems and data.
- Advanced Software Applications: Master the software applications used in modern auto repair shops.
9.2 Our Support Services
In addition to our training programs, we offer a range of support services to help you succeed.
- Technical Support: Get expert technical support when you need it.
- Remote Assistance: Receive remote assistance from our team of experienced technicians.
- Consulting Services: Get expert consulting services to help you optimize your operations.
10. Real-World Examples
Let’s look at some real-world examples of how blocking software with the Windows 10 Firewall can benefit auto repair shops.
10.1 Case Study 1: Preventing a Ransomware Attack
An auto repair shop was targeted by a ransomware attack. The attackers gained access to the shop’s network through a vulnerable software application. By blocking unauthorized software and monitoring network traffic, the shop was able to prevent the ransomware from spreading and encrypting their data.
10.2 Case Study 2: Securing Customer Data
An auto repair shop was concerned about the security of their customer data. They implemented a policy of blocking file-sharing applications and limiting access to customer data to only authorized personnel and software. As a result, they were able to prevent a data breach and protect their customers’ privacy.
10.3 Case Study 3: Controlling Software Usage
An auto repair shop was struggling to control software usage in their workshop. They implemented a policy of blocking unnecessary software and enforcing software policies through Group Policy. As a result, they were able to reduce their software licensing costs and improve their compliance with licensing agreements.
11. The Future of Firewall Management
The future of firewall management is likely to be characterized by increased automation, intelligence, and integration with other security tools.
11.1 AI and Machine Learning
AI and machine learning are being used to automate firewall management tasks, such as identifying and blocking malicious traffic.
- Automated Threat Detection: AI and machine learning algorithms can analyze network traffic in real-time to identify and block threats.
- Adaptive Firewall Rules: AI and machine learning can be used to create adaptive firewall rules that automatically adjust to changes in network traffic patterns.
- Predictive Security: AI and machine learning can be used to predict future security threats and proactively block them.
11.2 Cloud-Based Firewalls
Cloud-based firewalls offer several advantages over traditional firewalls, including scalability, flexibility, and cost-effectiveness.
- Scalability: Cloud-based firewalls can easily scale to meet the needs of growing businesses.
- Flexibility: Cloud-based firewalls can be deployed in a variety of environments, including public clouds, private clouds, and hybrid clouds.
- Cost-Effectiveness: Cloud-based firewalls can be more cost-effective than traditional firewalls, as they eliminate the need for expensive hardware and maintenance.
11.3 Integration with Other Security Tools
Firewalls are increasingly being integrated with other security tools, such as intrusion detection systems and security information and event management (SIEM) systems.
- Improved Threat Detection: Integration with other security tools can improve threat detection by providing a more comprehensive view of network activity.
- Automated Incident Response: Integration with other security tools can automate incident response by automatically blocking or isolating infected systems.
- Centralized Management: Integration with other security tools can provide centralized management of all security functions.
12. Frequently Asked Questions (FAQ)
Here are some frequently asked questions about blocking software with the Windows 10 Firewall.
12.1 Can I block system programs with the firewall?
Yes, but it’s generally not recommended. Blocking essential system programs can cause your computer to malfunction. Only block system programs if you are certain that they are not needed and are causing a security risk.
12.2 How do I know if a program is safe to allow through the firewall?
If you recognize the program and know that it’s from a trusted source, it’s generally safe to allow it through the firewall. If you’re unsure, research the program online or consult with a cybersecurity expert.
12.3 What should I do if I accidentally block an essential program?
If you accidentally block an essential program, you can create an exception rule to allow it to communicate. Follow the steps to create a new outbound or inbound rule, but in the Action step, select Allow the connection.
12.4 Can blocking a program slow down my computer?
In some cases, blocking a program can improve your computer’s performance by preventing it from consuming resources in the background. However, in other cases, it can cause the program to malfunction or slow down.
12.5 Is it possible to block a program temporarily?
Yes, you can temporarily disable a firewall rule to allow a program to communicate. In the Windows Defender Firewall with Advanced Security console, select the rule and click Disable in the right pane.
12.6 How often should I review my firewall rules?
It’s recommended to review your firewall rules at least once a quarter, or more frequently if you make significant changes to your network or software configurations.
12.7 What is the difference between inbound and outbound rules?
Inbound rules control incoming traffic to your computer, while outbound rules control outgoing traffic from your computer.
12.8 Can I use the Windows 10 Firewall to block websites?
The Windows 10 Firewall is primarily designed to block programs, not websites. To block websites, you can use a web filter or a third-party firewall that offers website blocking capabilities.
12.9 Does blocking a program prevent it from being installed?
No, blocking a program only prevents it from communicating over the network. It does not prevent it from being installed.
12.10 What are the best practices for naming firewall rules?
Use descriptive names that clearly identify the purpose of the rule. For example, “Block [Program Name] Outbound” or “Allow [Program Name] Inbound for Updates”.
13. Take Action Today!
Ready to take your auto repair skills to the next level? Visit CAR-REMOTE-REPAIR.EDU.VN today to learn more about our training programs and support services. Contact us at Whatsapp: +1 (641) 206-8880 or visit our location at 1700 W Irving Park Rd, Chicago, IL 60613, United States.
Don’t wait—secure your network and enhance your expertise with CAR-REMOTE-REPAIR.EDU.VN.
By following this comprehensive guide, you can effectively block software with the Windows 10 Firewall and protect your systems and data. Remember to regularly review your firewall rules and stay informed about the latest security threats.
