Are you searching for “Cara Hack Email Yahoo Dengan Software 2018” and hoping to gain access to an email account? While the idea might seem tempting, especially in scenarios like forgotten passwords or suspecting infidelity, attempting to hack into an email account, including Yahoo, is illegal and unethical. Instead, at CAR-REMOTE-REPAIR.EDU.VN, we focus on ethical practices and offer alternative solutions for legitimate needs within the automotive repair industry. Exploring advanced remote diagnostic tools or enhancing cybersecurity awareness within your shop are more productive and ethical paths. Learn about cybersecurity best practices, ethical hacking for security audits, and safe data handling.
Contents
- 1. Why You Should Avoid “Cara Hack Email Yahoo Dengan Software 2018”
- 1.1 The Legal Repercussions
- 1.2 The Ethical Considerations
- 1.3 Real-World Consequences
- 2. Why “Software 2018” is Irrelevant and Dangerous
- 2.1 Outdated Software is Ineffective
- 2.2 Risk of Malware and Viruses
- 2.3 Exposure to Legal Risks
- 2.4 Alternative Ethical Solutions
- 3. Legitimate Reasons for Wanting Access and Ethical Solutions
- 3.1 Forgotten Password
- 3.2 Deceased Family Member
- 3.3 Child’s Account
- 3.4 Business Account
- 4. Understanding Email Security and Why Hacking is Difficult
- 4.1 Password Encryption
- 4.2 Two-Factor Authentication (2FA)
- 4.3 IP Address Monitoring
- 4.4 Machine Learning and AI
- 4.5 Alternative Practices
- 5. CAR-REMOTE-REPAIR.EDU.VN: Focusing on Ethical and Secure Practices
- 5.1 Our Ethical Stance
- 5.2 Cybersecurity Training for Automotive Technicians
- 5.3 Remote Diagnostic Tools and Security
- 5.4 Data Protection Policies
- 5.5 Building a Secure Automotive Ecosystem
- 6. Alternative Legal and Ethical Solutions
- 6.1 Password Recovery Options
- 6.2 Legal Investigations
- 6.3 Parental Control Software
- 6.4 Business Account Access Policies
- 6.5 Enhancing Cybersecurity Knowledge and Awareness
- 7. Consequences of Getting Caught Hacking
- 7.1 Legal Consequences
- 7.2 Financial Consequences
- 7.3 Professional Consequences
- 7.4 Personal Consequences
- 7.5 Alternative Actions
- 8. How to Protect Your Own Yahoo Email Account
- 8.1 Strong Passwords
- 8.2 Two-Factor Authentication (2FA)
- 8.3 Email Security Settings
- 8.4 Phishing Awareness
- 8.5 Update Software
- 8.6 Additional Strategies
- 9. FAQ: Cara Hack Email Yahoo Dengan Software 2018
- 9.1 Is it possible to hack a Yahoo email using software from 2018?
- 9.2 What are the legal consequences of trying to hack a Yahoo email account?
- 9.3 Are there ethical ways to access someone’s Yahoo email account?
- 9.4 How can I recover my Yahoo email password if I’ve forgotten it?
- 9.5 What is two-factor authentication (2FA) and how does it protect my Yahoo email account?
- 9.6 How can I protect my Yahoo email account from phishing scams?
- 9.7 What should I do if I suspect someone has hacked my Yahoo email account?
- 9.8 Can CAR-REMOTE-REPAIR.EDU.VN help me hack into someone’s Yahoo email account?
- 9.9 What kind of cybersecurity training does CAR-REMOTE-REPAIR.EDU.VN offer?
- 9.10 Why is it important for automotive technicians to be aware of cybersecurity?
- 10. Conclusion
1. Why You Should Avoid “Cara Hack Email Yahoo Dengan Software 2018”
Hacking into someone’s email account, regardless of the tool or year, carries significant legal and ethical implications. Understanding these repercussions is crucial before even considering such actions.
1.1 The Legal Repercussions
Engaging in unauthorized access to email accounts can lead to severe legal penalties.
- Federal Laws: In the United States, laws like the Computer Fraud and Abuse Act (CFAA) criminalize accessing a computer without authorization or exceeding authorized access. Violating the CFAA can result in hefty fines and imprisonment.
- State Laws: Many states also have their own laws against computer hacking and unauthorized access to electronic data. These laws often mirror federal statutes but can sometimes carry additional or stricter penalties.
- International Laws: Depending on your location and the location of the email server, international laws may also apply. Many countries have similar laws criminalizing unauthorized computer access.
1.2 The Ethical Considerations
Beyond the legal ramifications, hacking into an email account raises serious ethical concerns.
- Violation of Privacy: Everyone has a right to privacy, and accessing their email without permission is a direct violation of that right. It’s akin to reading someone’s personal diary or intercepting their mail.
- Breach of Trust: Hacking can destroy relationships and erode trust. Whether it’s a personal or professional relationship, the act of secretly accessing someone’s private communications can cause irreparable damage.
- Damage to Reputation: Being caught hacking can severely damage your reputation. It can affect your career prospects, social standing, and personal relationships.
1.3 Real-World Consequences
The consequences of hacking can extend beyond legal and ethical concerns, affecting your personal and professional life.
- Job Loss: If you’re caught hacking at work or using company resources for illegal activities, you could lose your job and face difficulties finding future employment.
- Academic Penalties: Students caught hacking could face expulsion from school and damage to their academic record.
- Financial Penalties: Legal fines and potential civil lawsuits can result in significant financial burdens.
- Criminal Record: A criminal record can impact your ability to travel, obtain certain licenses, and even rent an apartment.
Ethical hacking and cybersecurity awareness promote responsible technology use and protect against legal and personal risks.
2. Why “Software 2018” is Irrelevant and Dangerous
The phrase “cara hack email Yahoo dengan software 2018” suggests using outdated tools for hacking. This approach is not only ineffective but also highly risky.
2.1 Outdated Software is Ineffective
Cybersecurity measures are constantly evolving, and older software is unlikely to bypass modern security protocols.
- Evolving Security: Email providers like Yahoo continuously update their security systems to protect against hacking attempts. Software from 2018 is unlikely to be effective against these advanced defenses.
- Patching Vulnerabilities: As vulnerabilities are discovered, software companies release patches to fix them. Older software lacks these updates, making it more susceptible to detection and prevention.
- Improved Detection Systems: Modern security systems are better at detecting and blocking hacking attempts. Using outdated software increases the likelihood of being caught.
2.2 Risk of Malware and Viruses
Downloading and using hacking software from untrusted sources can expose your computer to malware and viruses.
- Bundled Malware: Many so-called “hacking tools” are actually Trojan horses designed to install malware on your system. This malware can steal your personal information, damage your files, or even give hackers remote access to your computer.
- Phishing Scams: Websites offering hacking software often use phishing tactics to trick you into providing your email address and password. This information can then be used to hack your own accounts.
- Lack of Support: Outdated software is no longer supported by its developers, meaning there are no security updates or bug fixes. This makes it an easy target for hackers.
2.3 Exposure to Legal Risks
Using hacking software, regardless of its age, can increase your legal risk.
- Evidence of Intent: Downloading and using hacking software can be seen as evidence of intent to commit a crime. This can make it harder to defend yourself if you’re accused of hacking.
- Tracking and Tracing: Even if the software doesn’t work, your activities may be logged and traced back to you. This can provide law enforcement with the evidence they need to prosecute you.
- Increased Scrutiny: Using hacking software can put you on the radar of law enforcement and cybersecurity agencies. This can lead to increased scrutiny of your online activities.
2.4 Alternative Ethical Solutions
Instead of resorting to illegal hacking methods, explore ethical and legal alternatives for your needs.
- Password Recovery: If you’ve forgotten your Yahoo password, use the official password recovery options provided by Yahoo. This usually involves answering security questions or receiving a verification code by email or phone.
- Legal Investigations: If you suspect someone is engaging in illegal activities, contact law enforcement or a private investigator. They can use legal means to gather evidence and take appropriate action.
- Cybersecurity Awareness: Educate yourself and your employees about cybersecurity best practices. This can help prevent hacking attempts and protect your sensitive information.
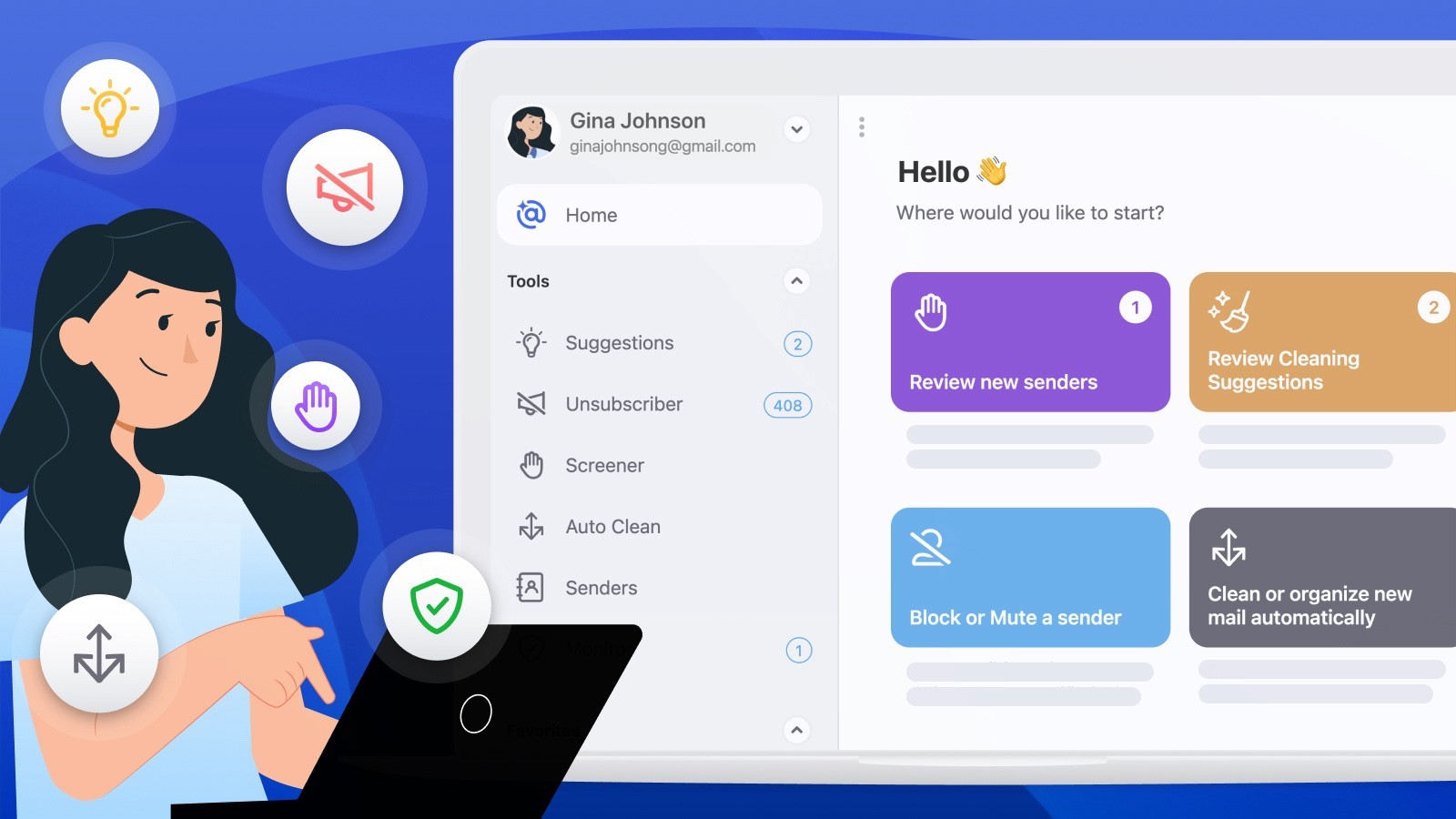 Cybersecurity and Ethical Hacking
Cybersecurity and Ethical Hacking
Ethical cybersecurity practices, like those taught at CAR-REMOTE-REPAIR.EDU.VN, focus on defense and prevention, not illegal intrusion.
3. Legitimate Reasons for Wanting Access and Ethical Solutions
While “cara hack email Yahoo dengan software 2018” is not a viable or ethical option, there are legitimate reasons why someone might need access to an email account. Here are some scenarios and ethical solutions:
3.1 Forgotten Password
Scenario: You’ve forgotten your Yahoo email password and can’t access your account.
Ethical Solution:
- Yahoo’s Password Recovery: Use Yahoo’s official password recovery process. This typically involves answering security questions, providing an alternate email address, or receiving a verification code via SMS.
- Account Recovery Form: If you can’t remember your security questions or don’t have access to your recovery email or phone, fill out Yahoo’s account recovery form. Provide as much information as possible to help them verify your identity.
- Contact Yahoo Support: If all else fails, contact Yahoo’s customer support for assistance. Be prepared to provide proof of your identity and ownership of the account.
3.2 Deceased Family Member
Scenario: You need access to a deceased family member’s Yahoo email account for legal or personal reasons.
Ethical Solution:
- Yahoo’s Deceased Account Policy: Contact Yahoo’s customer support and inquire about their policy for handling deceased accounts. They may require a death certificate and legal documentation, such as a will or court order.
- Legal Representation: Consult with an attorney who can help you navigate the legal process of obtaining access to the account. They can advise you on the necessary documentation and represent you in court if necessary.
- Respect Privacy: Remember to respect the deceased person’s privacy and only access the account for legitimate purposes. Avoid sharing personal information or engaging in activities that could harm their reputation.
3.3 Child’s Account
Scenario: You need access to your child’s Yahoo email account to monitor their online activity and protect them from harm.
Ethical Solution:
- Parental Consent: If your child is a minor, obtain their consent before accessing their account. Explain why you need access and assure them that you’re doing it to protect them.
- Shared Account: Consider creating a shared email account that both you and your child can access. This allows you to monitor their communications without infringing on their privacy.
- Parental Control Software: Use parental control software to monitor your child’s online activity, block inappropriate content, and set time limits. This can help you protect them without having to constantly monitor their email.
3.4 Business Account
Scenario: You need access to a former employee’s Yahoo email account for business purposes, such as retrieving important documents or communicating with clients.
Ethical Solution:
- Company Policy: Ensure your company has a clear policy regarding access to employee email accounts after they leave the company. This policy should be communicated to all employees and included in their employment contracts.
- Legal Counsel: Consult with an attorney to ensure you’re complying with all applicable laws and regulations. They can advise you on the proper procedures for accessing the account and handling sensitive information.
- Limited Access: Only access the account for legitimate business purposes and avoid accessing personal emails or communications. Document all actions taken and maintain a clear audit trail.
 Legitimate Access Solutions
Legitimate Access Solutions
Ethical and legal solutions for accessing email accounts prioritize privacy and compliance, offering responsible alternatives to hacking.
4. Understanding Email Security and Why Hacking is Difficult
Modern email services like Yahoo employ robust security measures to protect user accounts from unauthorized access. Understanding these measures can help you appreciate why hacking is difficult and why ethical solutions are the best approach.
4.1 Password Encryption
Email providers use advanced encryption algorithms to protect passwords stored on their servers.
- Hashing: Instead of storing passwords in plain text, they are converted into a unique string of characters using a hashing algorithm. This makes it difficult to reverse-engineer the original password even if the database is compromised.
- Salting: A random string of characters, known as a “salt,” is added to each password before it is hashed. This makes it more difficult for hackers to use pre-computed tables of hashes to crack passwords.
- Key Stretching: Key stretching algorithms are used to increase the time it takes to crack a password. This makes it more difficult for hackers to use brute-force attacks to guess passwords.
4.2 Two-Factor Authentication (2FA)
2FA adds an extra layer of security to your email account by requiring you to provide a second form of authentication in addition to your password.
- SMS Codes: A verification code is sent to your mobile phone via SMS each time you log in. You must enter this code in addition to your password to access your account.
- Authenticator Apps: Authenticator apps like Google Authenticator or Authy generate a unique code that changes every 30 seconds. You must enter this code in addition to your password to access your account.
- Hardware Security Keys: Hardware security keys like YubiKey are physical devices that you plug into your computer to verify your identity. These keys provide the highest level of security against phishing and other attacks.
4.3 IP Address Monitoring
Email providers monitor IP addresses to detect suspicious login activity.
- Login Location: If you log in from a new location, the email provider may require you to verify your identity by answering security questions or receiving a verification code.
- Login Frequency: If you log in too many times in a short period, the email provider may temporarily lock your account to prevent brute-force attacks.
- Suspicious Activity: If the email provider detects suspicious activity, such as a sudden change in login location or a large number of failed login attempts, they may temporarily lock your account and require you to verify your identity.
4.4 Machine Learning and AI
Email providers use machine learning and artificial intelligence to detect and prevent hacking attempts.
- Anomaly Detection: Machine learning algorithms can detect anomalies in user behavior, such as unusual login patterns or suspicious email content.
- Phishing Detection: AI-powered systems can analyze email content to identify phishing scams and block them before they reach your inbox.
- Spam Filtering: Machine learning algorithms are used to filter spam and prevent it from reaching your inbox.
4.5 Alternative Practices
Here are some alternative cybersecurity practices to enhance your security posture:
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure that your systems are protected against the latest threats.
- Penetration Testing: Hire ethical hackers to conduct penetration testing and simulate real-world attacks.
- Employee Training: Provide regular cybersecurity training to your employees and educate them about the latest threats and best practices.
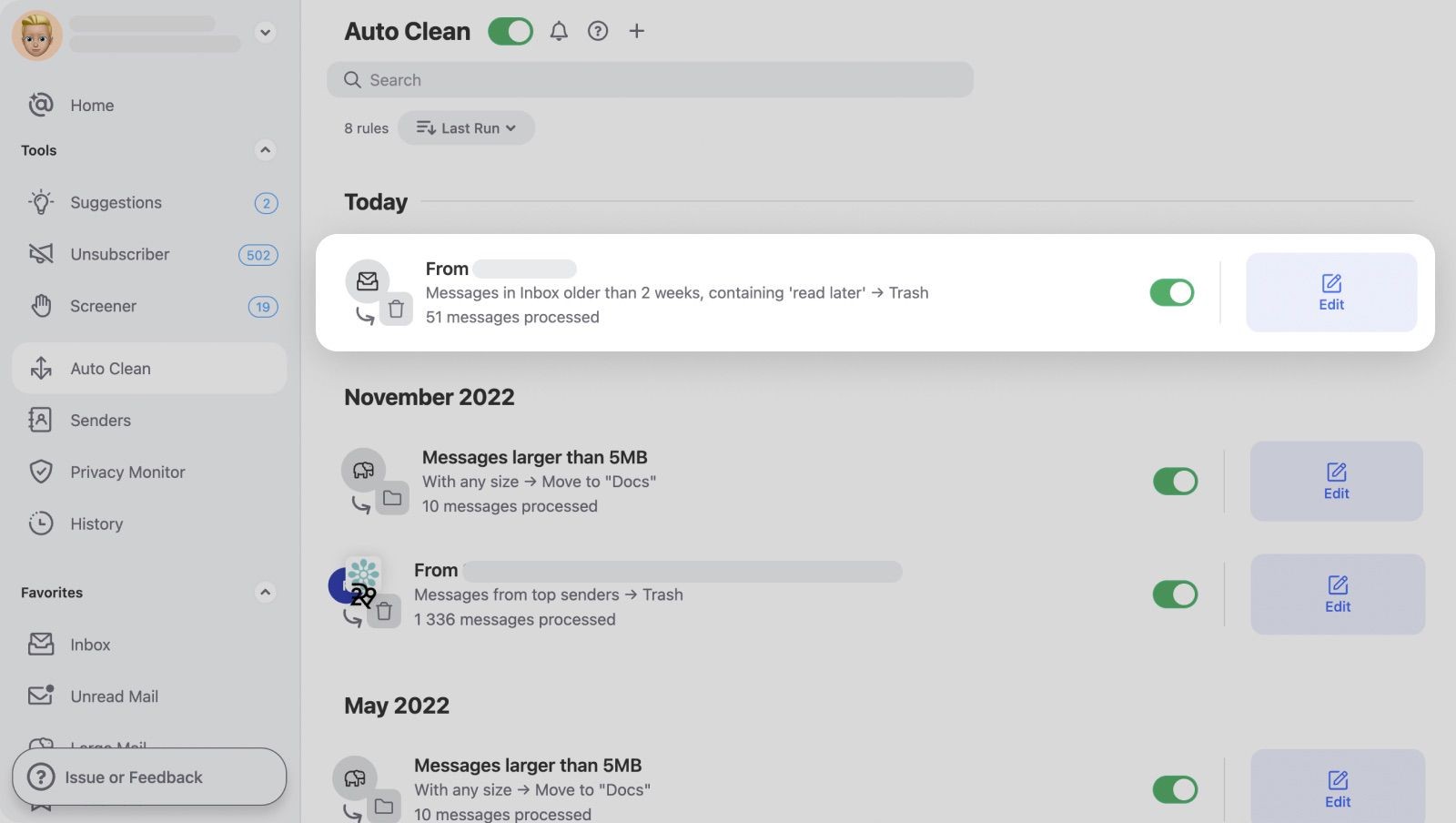 Email Security Measures
Email Security Measures
Modern email security measures make hacking difficult and highlight the importance of ethical and legal alternatives for accessing accounts.
5. CAR-REMOTE-REPAIR.EDU.VN: Focusing on Ethical and Secure Practices
At CAR-REMOTE-REPAIR.EDU.VN, we emphasize ethical and secure practices in all aspects of automotive repair and technology. Our commitment to these principles extends to cybersecurity awareness and responsible data handling.
5.1 Our Ethical Stance
We firmly believe that ethical behavior is essential in all aspects of our work. This includes respecting privacy, complying with the law, and using technology responsibly.
- Integrity: We conduct our business with the highest level of integrity and transparency. We are committed to doing the right thing, even when it’s difficult.
- Respect for Privacy: We respect the privacy of our customers, employees, and partners. We are committed to protecting their personal information and using it only for legitimate purposes.
- Compliance with the Law: We comply with all applicable laws and regulations. We are committed to operating our business in a legal and ethical manner.
5.2 Cybersecurity Training for Automotive Technicians
We offer cybersecurity training for automotive technicians to help them protect themselves and their customers from cyber threats.
- Understanding Cybersecurity Threats: Our training covers the latest cybersecurity threats facing the automotive industry, including malware, phishing, and hacking.
- Best Practices for Data Security: We teach technicians best practices for protecting customer data, including password security, data encryption, and access control.
- Secure Remote Diagnostics: We provide training on how to perform remote diagnostics securely and protect against unauthorized access to vehicle systems.
5.3 Remote Diagnostic Tools and Security
We offer remote diagnostic tools that are designed with security in mind. These tools use encryption and other security measures to protect against unauthorized access to vehicle systems.
- Secure Communication Protocols: Our remote diagnostic tools use secure communication protocols to encrypt data transmitted between the technician and the vehicle.
- Access Control: We use access control mechanisms to ensure that only authorized technicians can access vehicle systems.
- Audit Trails: Our remote diagnostic tools maintain detailed audit trails of all actions taken, allowing us to track and investigate any suspicious activity.
5.4 Data Protection Policies
We have data protection policies in place to protect the personal information of our customers and employees.
- Data Minimization: We only collect the data that is necessary for legitimate business purposes.
- Data Encryption: We encrypt sensitive data both in transit and at rest.
- Access Control: We restrict access to personal data to authorized personnel only.
- Data Retention: We retain personal data only for as long as necessary to fulfill the purposes for which it was collected.
5.5 Building a Secure Automotive Ecosystem
By focusing on ethical practices, cybersecurity training, and secure remote diagnostic tools, we are helping to build a more secure automotive ecosystem.
- Protecting Customers: We are committed to protecting our customers from cyber threats and ensuring the safety and security of their vehicles.
- Empowering Technicians: We are empowering automotive technicians with the knowledge and tools they need to protect themselves and their customers from cyber threats.
- Promoting Ethical Behavior: We are promoting ethical behavior throughout the automotive industry and encouraging others to adopt responsible data handling practices.
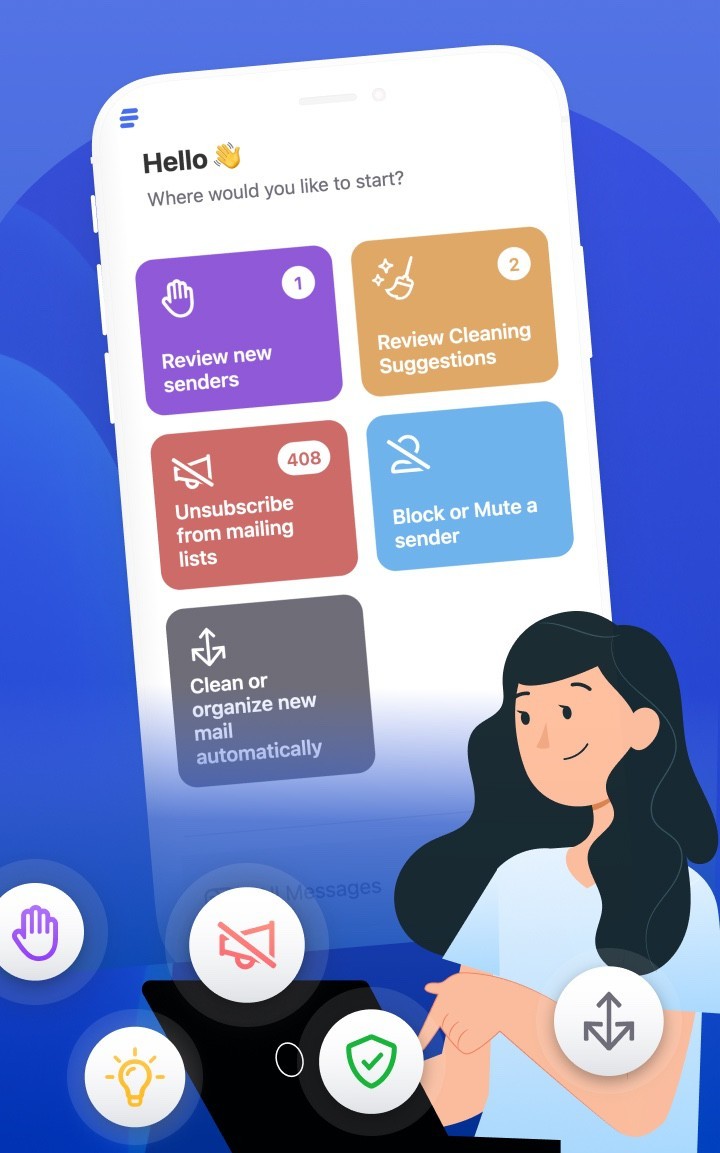 CAR-REMOTE-REPAIR.EDU.VN Commitment
CAR-REMOTE-REPAIR.EDU.VN Commitment
CAR-REMOTE-REPAIR.EDU.VN promotes ethical, secure automotive practices through training, tools, and robust data protection policies, building a safer industry.
6. Alternative Legal and Ethical Solutions
Instead of searching for “cara hack email Yahoo dengan software 2018,” consider these legitimate and ethical ways to achieve your goals:
6.1 Password Recovery Options
If you’ve forgotten your password, use Yahoo’s official password recovery options.
- Security Questions: Answer the security questions you set up when you created your account.
- Alternate Email: Receive a password reset link at your alternate email address.
- SMS Verification: Receive a verification code via SMS on your mobile phone.
6.2 Legal Investigations
If you suspect someone is engaging in illegal activities, contact law enforcement or a private investigator.
- Law Enforcement: Report the suspected illegal activity to law enforcement and provide them with any evidence you have.
- Private Investigator: Hire a licensed private investigator to gather evidence and conduct surveillance.
6.3 Parental Control Software
If you’re concerned about your child’s online activity, use parental control software to monitor their communications and block inappropriate content.
- Monitoring Tools: Use monitoring tools to track your child’s online activity, including email, social media, and web browsing.
- Content Filtering: Use content filtering to block inappropriate websites and content.
- Time Limits: Set time limits for your child’s online activity.
6.4 Business Account Access Policies
If you need access to a former employee’s email account, follow your company’s established policies and procedures.
- Company Policy: Review your company’s policy on access to employee email accounts after they leave the company.
- Legal Counsel: Consult with an attorney to ensure you’re complying with all applicable laws and regulations.
- Limited Access: Only access the account for legitimate business purposes and avoid accessing personal emails or communications.
6.5 Enhancing Cybersecurity Knowledge and Awareness
Invest in training to enhance your knowledge on cybersecurity measures to prevent these issues.
- Online Courses: Take online courses on cybersecurity and data protection to enhance your knowledge and skills.
- Industry Certifications: Pursue industry certifications such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH).
- Stay Informed: Stay up-to-date on the latest cybersecurity threats and best practices by reading industry publications and attending conferences.
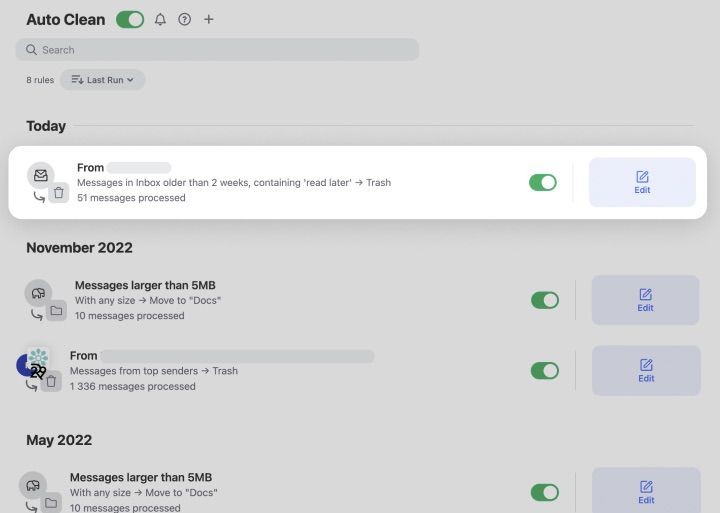 Ethical Alternatives
Ethical Alternatives
Explore ethical and legal alternatives like password recovery, legal investigations, parental control, and cybersecurity awareness to achieve your goals responsibly.
7. Consequences of Getting Caught Hacking
Engaging in hacking activities can lead to severe consequences, both legally and personally.
7.1 Legal Consequences
Hacking is a crime that can result in significant legal penalties.
- Criminal Charges: You could face criminal charges under laws like the Computer Fraud and Abuse Act (CFAA) and state computer crime laws.
- Fines: Conviction for hacking can result in hefty fines.
- Imprisonment: Depending on the severity of the offense, you could face imprisonment.
- Criminal Record: A criminal record can make it difficult to get a job, rent an apartment, or travel internationally.
7.2 Financial Consequences
Hacking can also lead to significant financial losses.
- Legal Fees: You’ll need to hire an attorney to defend yourself against criminal charges, which can be expensive.
- Civil Lawsuits: You could be sued by the victim of the hacking for damages, including lost income, emotional distress, and reputational harm.
- Restitution: You may be ordered to pay restitution to the victim of the hacking to cover their financial losses.
7.3 Professional Consequences
Hacking can have a devastating impact on your career.
- Job Loss: You could lose your job if you’re caught hacking, especially if you’re using company resources or accessing company data.
- Reputational Damage: Your reputation could be irreparably damaged, making it difficult to find future employment.
- Loss of Licenses: If you’re a licensed professional, such as a doctor, lawyer, or engineer, you could lose your license.
7.4 Personal Consequences
Hacking can also have a negative impact on your personal life.
- Relationship Damage: Hacking can damage your relationships with family and friends.
- Social Stigma: You could face social stigma and isolation.
- Emotional Distress: You could experience emotional distress, anxiety, and depression.
7.5 Alternative Actions
If you are worried about your cybersecurity, consider the following measures:
- Strong Password Creation: Generate strong, unique passwords for all of your online accounts.
- Regular Monitoring: Regularly monitor your accounts for suspicious activity.
- Prompt Reporting: Promptly report any suspected hacking attempts to law enforcement and the affected service providers.
 Consequences of Hacking
Consequences of Hacking
Hacking carries severe legal, financial, professional, and personal consequences, emphasizing the importance of ethical and legal online behavior.
8. How to Protect Your Own Yahoo Email Account
Protecting your own Yahoo email account from hacking is crucial. Here are some steps you can take to enhance your security:
8.1 Strong Passwords
Use strong, unique passwords for your Yahoo email account.
- Password Length: Aim for at least 12 characters.
- Character Variety: Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Avoid Personal Information: Don’t use personal information like your name, birthday, or pet’s name.
- Unique Passwords: Use a different password for each of your online accounts.
8.2 Two-Factor Authentication (2FA)
Enable two-factor authentication (2FA) for your Yahoo email account.
- SMS Codes: Receive a verification code via SMS on your mobile phone each time you log in.
- Authenticator Apps: Use an authenticator app like Google Authenticator or Authy to generate a unique code that changes every 30 seconds.
- Hardware Security Keys: Use a hardware security key like YubiKey for the highest level of security.
8.3 Email Security Settings
Configure your Yahoo email security settings to enhance protection.
- Account Activity: Review your account activity regularly to check for suspicious logins.
- Recovery Information: Keep your recovery email address and phone number up-to-date.
- App Passwords: Use app passwords for third-party applications to prevent them from accessing your main account password.
8.4 Phishing Awareness
Be aware of phishing scams and avoid clicking on suspicious links or attachments.
- Verify Sender: Verify the sender’s email address before clicking on any links or attachments.
- Look for Red Flags: Look for red flags like spelling errors, grammatical mistakes, and urgent requests for personal information.
- Don’t Provide Personal Information: Never provide personal information like your password, social security number, or credit card number in response to an email.
8.5 Update Software
Keep your operating system, web browser, and email client up-to-date with the latest security patches.
- Automatic Updates: Enable automatic updates to ensure that you always have the latest security patches.
- Regular Scans: Run regular virus scans to detect and remove malware.
- Firewall Protection: Use a firewall to protect your computer from unauthorized access.
8.6 Additional Strategies
Here are some additional cybersecurity strategies that can help protect you:
- Use a VPN: Use a virtual private network (VPN) to encrypt your internet traffic and protect your privacy.
- Monitor Credit Reports: Regularly monitor your credit reports for signs of identity theft.
- Identity Theft Protection: Consider purchasing identity theft protection services.
Enhance your Yahoo email security with strong passwords, 2FA, secure settings, phishing awareness, and updated software to safeguard against hacking.
9. FAQ: Cara Hack Email Yahoo Dengan Software 2018
9.1 Is it possible to hack a Yahoo email using software from 2018?
No, it is highly unlikely. Modern email providers like Yahoo have significantly enhanced their security measures since 2018, making outdated software ineffective.
9.2 What are the legal consequences of trying to hack a Yahoo email account?
Attempting to hack an email account can lead to criminal charges, hefty fines, imprisonment, and a criminal record.
9.3 Are there ethical ways to access someone’s Yahoo email account?
Yes, there are ethical ways, such as using Yahoo’s official password recovery options, obtaining legal authorization, or parental consent.
9.4 How can I recover my Yahoo email password if I’ve forgotten it?
Use Yahoo’s official password recovery process, which typically involves answering security questions, providing an alternate email address, or receiving a verification code via SMS.
9.5 What is two-factor authentication (2FA) and how does it protect my Yahoo email account?
2FA adds an extra layer of security by requiring you to provide a second form of authentication, such as an SMS code or authenticator app code, in addition to your password.
9.6 How can I protect my Yahoo email account from phishing scams?
Be cautious of suspicious emails, verify the sender’s address, look for red flags like spelling errors, and never provide personal information in response to an email.
9.7 What should I do if I suspect someone has hacked my Yahoo email account?
Change your password immediately, enable two-factor authentication, review your account activity, and report the incident to Yahoo.
9.8 Can CAR-REMOTE-REPAIR.EDU.VN help me hack into someone’s Yahoo email account?
No, CAR-REMOTE-REPAIR.EDU.VN does not provide any services or information related to hacking. We focus on ethical practices, cybersecurity awareness, and secure remote diagnostic tools for the automotive industry.
9.9 What kind of cybersecurity training does CAR-REMOTE-REPAIR.EDU.VN offer?
We offer cybersecurity training for automotive technicians that covers understanding cybersecurity threats, best practices for data security, and secure remote diagnostics.
9.10 Why is it important for automotive technicians to be aware of cybersecurity?
Automotive technicians handle sensitive customer data and have access to vehicle systems, making them potential targets for cyberattacks. Cybersecurity awareness helps them protect themselves and their customers from cyber threats.
10. Conclusion
The search for “cara hack email Yahoo dengan software 2018” is not only misguided but also potentially dangerous and illegal. Instead of pursuing unethical and ineffective methods, focus on ethical solutions, legal alternatives, and proactive measures to protect your own email account and data. At CAR-REMOTE-REPAIR.EDU.VN, we are committed to promoting ethical practices, providing cybersecurity training, and developing secure remote diagnostic tools for the automotive industry. Embrace responsible technology use and stay informed about the latest cybersecurity threats and best practices to build a safer and more secure digital world.
Interested in enhancing your cybersecurity knowledge or learning more about our secure remote diagnostic tools? Visit CAR-REMOTE-REPAIR.EDU.VN to explore our training programs and services. Contact us at Address: 1700 W Irving Park Rd, Chicago, IL 60613, United States or Whatsapp: +1 (641) 206-8880.